Local and State Police are Joining Trump’s Deportation Force
Francesca D’Annunzio, David McHam Investigative Reporting Fellow - Texas Observer
_Stephan: Here is the fact-based truth about what is going on with deportation. Two things stand out for me. The first is that the Trump coup is actually deporting fewer people than Biden’s presidency did. The second is that Trump is now basically militarizing local and state police exactly as Hitler did. If you track the … ⌘ Read more
Erlang Solutions: Top 5 IoT Business Security Basics
IoT is now a fundamental part of modern business. With more than 17 billion connected devices worldwide, IoT business security is more important than ever. A single breach can expose sensitive data, disrupt operations, and damage a company’s reputation.
To help safeguard your business, we’ll cover five essential IoT security basics: data encryption, strong password policies, regular security audits, employee awareness tr … ⌘ Read more
@prologic@twtxt.net Tolerant yes, but in the right places. This is just encouraging people to not properly care. The extreme end is HTML where parsers basically accept any input. I’m not a fan of that. Whatever.
McMahon Hearing Shows Trump ‘Dead Set on Destroying Public Education’
Jessica Corbett, Senior Editor - Common Dreams
_Stephan: Another MAGAt lackey testifies basically to her intent to destroy public education. It is part of the coup we are undergoing. It has not passed notice of the oligarchs that the less well-educated men and women are the more likely it is that they will vote for Republicans. That’s why they want to end public education. It not only … ⌘ Read more
@andros@twtxt.andros.dev I suggest to not touch it and work on a different project instead. :-D
No, in all seriousness, that’s a tough one. Try to figure out the requirements and write tests to cover them. In my experience, if there is no good documention, tests might also be lacking. It goes without saying that you have to understand the code segments first before you can begin to refactor them. Commit even earlier and more often than usual, this will help you bisecting potentially introduced bugs later on. Basically baby steps.
But it also depends on the amount of refactoring required. Maybe just scrap it entirely and start from scratch. This might not be feasible due to e.g. the overall project size, though.
Pineboards Introduces Modulo Carrier Boards for Raspberry Pi CM5 and CM4
Pineboards has introduced the Modulo4, Modulo5 Basic, and Modulo5 IO PoE+ carrier boards, adapting Raspberry Pi Compute Modules to the Raspberry Pi 5 form factor. These boards maintain compatibility with PCIe HATs, cases, and cooling solutions, with the Modulo5 IO PoE+ adding PoE+ support for network-powered operation. Pineboards indicates that with the release of the […] ⌘ Read more
(#elzuxba) @thecanine@thecanine The thing is, all these IVR phone systems are so fucking useless it’s not even funny. They either can’t understa …
@thecanine @twtxt.net The thing is, all these IVR phone systems are so fucking useless it’s not even funny. They either can’t understand you, are stupid as fuck, or somewhere in between. You spend minutes to hours trying to figure out how to get anywhere you basically just end up giving up. I think it’s done on purpose 😱 ⌘ Read more
@arne@uplegger.eu Ohjemine, TYPO3! O_o Lass mich schreiend davonlaufen!
Mit dieser absoluten Katastrophensoftware vor dem Herrn haben wir mal ein Studienprojekt gemacht. Die hat alle Vorurteile komplett übererfüllt. Angefangen von Fehlerseiten, die statt 4xx oder dergleichen immer mit HTTP 200 ausgeliefert wurden oder auch, dass das generierte HTML leider einfach ungültig war. Über die Implementierung von Löschen durch einen Deleted-Schalter in der Datenbank, das Speichern von Passwörtern im Klartext bis hin zu völlig umständlichen Bedienungskonzepten. Alles hat immer brutal viele Schritte gebraucht. Das Zeilennummernrumgeeier im TYPO-Script erinnerte eher an Basic. Uns kam es auch so vor, als ob man damit nicht ernsthaft was sinnvolles machen könnte.
Zu allem Überfluss hatte irgendwer noch ein ganz hundsmiserables Buch ausgegraben, das als Vorbereitung dienen sollte. Ich kann mich zum Glück weder an den Titel noch den Autor erinnern, aber ich weiß noch, wie das komplett inkonsistent geschrieben war. Anfangs gabs mehrere Seiten zu Unicode und UTF-8 wurde angepriesen, aber alle Beispiele haben dann auf ISO-8859-1 gesetzt. Gezeigter Beispielcode war häufig unterste Schublade. Selten hab ich so merkwürdige Erklärungen gelesen: „Wenn Sie die Sicherheitswarnhinweise stören, kommentieren Sie doch bitte im Quelltext die die()-Funktion in $ZEILE aus.“ Oder ein anderer Klassiker: „Ausgeschrieben würde der Code wohl folgendes tun…“. War sich der Autor also nicht ganz sicher, ob sein Codeschnipsel vllt. doch in Wahrheit was ganz anderes tut.
Seit diesem gigantischen Trauma (das hat mich wirklich sehr nachhaltig geprägt, wie man Dinge nicht machen sollte) hab ich erfolgreich einen Bogen um das TYPO3-Universum gemacht.
Ich kann nur hoffen, dass es zwischenzeitlich ein wenig besser geworden ist. Aber Deinem Kurzbericht zufolge scheint da ja immer noch der Wurm drin zu sein. Mein Beileid! :-(
For many years I have found Flask to be too basic a tool for modern development. But since I create APIs using Flask with Pydantic to validate the input data, some middlewares for parsing and Blueprint to separate the code into modules… I must admit that I am super comfortable, fast and easy to test.
#flask #python #pydantic
Federal Judge Temporarily Blocks Trump Administration Freeze On Federal Grants And Loans
JoNel Aleccia, Moriah Balingit, Collin Binkley, Matthew Daly, Lisa Mascaro, Adithi Ramakrishnan, Amanda Seitz, Michael Sisak, Lindsay Whitehurst and Tammy Weber, Reporters - Huffington Post | Associated Press
_Stephan: Criminal Trump basically shut down the government today, despite his administration’s denial, but this move has been blocked by … ⌘ Read more
Federal DEI websites go dark after Trump order and threat of ‘consequences’
Robert King and Ben Leonard, - Politico
Stephan: In full accord with Project 2025, the American government is being restructured so that only Whites, and preferably males, are treated fairly. All DEI issues or basic civil rights are no longer protected. The United States is becoming South Africa in the 1960s.

^-- SC2046: Quote this to prevent word splitting.
For more information:
https://www.shellcheck.net/wiki/SC2046 -- Quote this to prevent word splitt...
Most likely not all that problematic in this application, but it’s good to know about this underlying concept. Word splitting is basically splitting tokens on whitespace, this can lead to interesting consequences as illustrated by this little code:
$ echo $(echo "Hello World")
Hello World
$ echo "$(echo "Hello World")"
Hello World
In the first case the shells sees two whitespace-separated tokens or arguments for the echo command. This basically becomes echo Hello World. So, echo joins them by a single space. In the second one it sees one argument for the echo command, so echo simply echos this single argument that contains three spaces.
@kat@yarn.girlonthemoon.xyz definitely a fun way to get better at bash scripting by hand (AKA learn how it works besides the extreme basics i know) and use gum to make them cute too
**(#7xqzija) I’m just basically learning now how ModSecurity rules work and how to write my own.
The builtin OWASP rules are already working nice …**
I’m just basically learning now how ModSecurity rules work and how to write my own.
The builtin OWASP rules are already working nicely 👌 – And yeah I won’t include the WAF on every site block, probably just my main/primary domain where I tend to run demo services and other things. ⌘ Read more
(#fgaa2na) A pointer is basically a reference to a variable. It is typically used with structs and especially in pointer receiver methods so tha …
A pointer is basically a reference to a variable. It is typically used with structs and especially in pointer receiver methods so that you can modify fields of a struct. ⌘ Read more
How women’s basic rights and freedoms are being eroded all over the world
, - The Conversation
_Stephan: Part of the manifestation of humanity’s precognition is the hysterical fear a growing number of men have about women. Part of it is, I think, that there is no other way to incarnate except through the body of a woman, and these men unconsciously realize if there is a subordinate gender it is male. So they seek control of their superiors. This i … ⌘ Read more
Enhance build security and reach SLSA Level 3 with GitHub Artifact Attestations
Learn how GitHub Artifact Attestations can enhance your build security and help your organization achieve SLSA Level 3. This post breaks down the basics of SLSA, explains the importance of artifact attestations, and provides a step-by-step guide to securing your build process.
The post [Enhance build security and reach SLSA Level 3 with GitHub Artifact Attest … ⌘ Read more
(#rcpphgq) @bender@bender It’s not super important, I tagged you on IRC, but essentially I’m trying to build a tilde (shared linux host) thin …
@bender It’s not super important, I tagged you on IRC, but essentially I’m trying to build a tilde (shared linux host) thingy of some sort 😅 just experimenting with an idea I’ve had a while back. See for example working trivial “Hello World” at http://mbox.blue/~prologic/ – The basic idea is that when you ssh -p 222 user@mbox.b … ⌘ Read more
haha, that’s gold xD.
#randomMemory I remember when I was starting to code, like 30 years ago, not understanding why my Basic file didn’t run when I renamed it to .exe
And nowadays, I’ve seen a few Go apps in a single executable, so twtxt.exe could be a thing, he!
Micropub test of creating a basic h-entry
Why Can’t I Access Control Center from iPhone Mirroring?
One of the best features of modern MacOS versions, from Sequoia 15.0 onward, is iPhone Mirroring, which allows Mac users to interact with their iPhone and use their iPhone directly from their Mac. iPhone Mirroring is almost entirely full featured in that you can access basically every iPhone feature from the Mac… but “almost entirely” … [Read More](https://osxdaily.com/2024/11/29/why-cant-i-access-control-center-from … ⌘ Read more
4rkal creates XMR ‘micro-tipping’ tool for P2Pool mini miners
4rkal1 has announced2 the beta release3 of Donate Monero Via P2Pool (DMVP2P) 4, a new tool that enables XMR micro-tipping via P2Pool mini 5 for miners on Linux and Windows:
Would love to get some feedback on a new project I started [..] Basically it’s a simple GUI that will allow you to mine to a certain users address via p2pool mini. Think monerodevs but donating via … ⌘ Read more
(#54eftcq) @gallowsgryph So he’s basically an asshole? 🤣
@gallowsgryph @prismdragon.net So he’s basically an asshole? 🤣 ⌘ Read more
The Australia Labor government, Albanese and the honourable Michelle Rowland federal member for parliament and communications minster are fuckin …
The Australia Labor government, Albanese and the honourable Michelle Rowland federal member for parliament and communications minster are fucking clowns. It’s stupid shit like this that’s the real problem with “big tech” social media platforms. These morons just simply don’t understand basic economics and basic business.
Why would a company like Meta, X a … ⌘ Read more
CNCF and Andela Announce Partnership to Train 20,000+ African Tech Professionals
The partnership will upskill African tech talent on Kubernetes basics; extend opportunity as global borderless workforces grow Salt Lake City, UT. – KubeCon + CloudNativeCon North America – November 15, 2024 – The Cloud Native Computing Foundation® (CNCF®),… ⌘ Read more
Righto, @eapl.me@eapl.me, ta for the writeup. Here we go. :-)
Metadata on individual twts are too much for me. I do like the simplicity of the current spec. But I understand where you’re coming from.
Numbering twts in a feed is basically the attempt of generating message IDs. It’s an interesting idea, but I reckon it is not even needed. I’d simply use location based addressing (feed URL + ‘#’ + timestamp) instead of content addressing. If one really wanted to, one could hash the feed URL and timestamp, but the raw form would actually improve disoverability and would not even require a richer client. But the majority of twtxt users in the last poll wanted to stick with content addressing.
yarnd actually sends If-Modified-Since request headers. Not only can I observe heaps of 304 responses for yarnds in my access log, but in Cache.FetchFeeds(…) we can actually see If-Modified-Since being deployed when the feed has been retrieved with a Last-Modified response header before: https://git.mills.io/yarnsocial/yarn/src/commit/98eee5124ae425deb825fb5f8788a0773ec5bdd0/internal/cache.go#L1278
Turns out etags with If-None-Match are only supported when yarnd serves avatars (https://git.mills.io/yarnsocial/yarn/src/commit/98eee5124ae425deb825fb5f8788a0773ec5bdd0/internal/handlers.go#L158) and media uploads (https://git.mills.io/yarnsocial/yarn/src/commit/98eee5124ae425deb825fb5f8788a0773ec5bdd0/internal/media_handlers.go#L71). However, it ignores possible etags when fetching feeds.
I don’t understand how the discovery URLs should work to replace the User-Agent header in HTTP(S) requests. Do you mind to elaborate?
Different protocols are basically just a client thing.
I reckon it’s best to just avoid mixing several languages in one feed in the first place. Personally, I find it okay to occasionally write messages in other languages, but if that happens on a more regularly basis, I’d definitely create a different feed for other languages.
Isn’t the emoji thing “just” a client feature? So, feed do not even have to state any emojis. As a user I’d configure my client to use a certain symbol for feed ABC. Currently, I can do a similar thing in tt where I assign colors to feeds. On the other hand, what if a user wants to control what symbol should be displayed, similar to the feed’s nick? Hmm. But still, my terminal font doesn’t even render most of emojis. So, Unicode boxes everywhere. This makes me think it should actually be a only client feature.
(#puqhbtq) @bender@bender I mean I’ve thought about it! It’s an intriguing idea to be able to have basic IP over HAM Radio 🤔
@bender I mean I’ve thought about it! It’s an intriguing idea to be able to have basic IP over HAM Radio 🤔 ⌘ Read more
(#k6y2oia) @sorenpeter@sorenpeter This is basically very similar to how WebFinger used by things like Mastodon and Salty.im amongst others.
@sorenpeter @darch.dk@darch.dk This is basically very similar to how WebFinger used by things like Mastodon and Salty.im amongst others. ⌘ Read more
(#b6juizq) @cuaxolotl The reason I ask is that I maintain the Twtxt search engine and crawler service that basically does exactly this, so I’m c …
@cuaxolotl @sunshinegardens.org The reason I ask is that I maintain the Twtxt search engine and crawler service that basically does exactly this, so I’m curious what you’re trying to solve by doing this yourself? Not that that’s a bad idea. I just want to understand what you are trying to achieve … ⌘ Read more
Erlang Solutions: Implementing Phoenix LiveView: From Concept to Production
When I began working with Phoenix LiveView, the project evolved from a simple backend service into a powerful, UI-driven customer service tool. A basic Phoenix app for storing user data quickly became a core part of our client’s workflow.
In this post, I’ll take you through a project that grew from its original purpose- from a service fo … ⌘ Read more
How to Fix “Recents” Folder Empty on Mac
The Mac “Recents” folder in Finder is a useful catchall Smart Folder that, as the name implies, contains all recently opened, modified, or added files that are found within the file system. This means the “Recents” folder should contain everything from text files, documents, PDFs, images, video, basically anything in the file system that has … Read More ⌘ Read more
How to Scroll-to-Top with Dynamic Island on iPhone 16, iPhone 15, & iPhone 14 Pro
Scroll-to-Top is a super useful gesture that has been around on the iPhone for a long time, basically rather than swiping to get back to the top of a long screen of text, email, webpage, or whatever, you just tap the top of the screen and it immediately scrolls to the top. This is a … [Read More](https://osxdaily.com/2024/10/14/how-to-scroll-to-top-with-dynamic-island-on … ⌘ Read more
I Went Back to Basics… ⌘ Read more
ki9 starts work on XMR price API with data from Bisq, Haveno-reto
Keith Irwin (ki91) has apparently started working on XMR Price F.Y.I. 2 - a new Monero price API with unbiased street price data from multiple sources, including Haveno-reto 3 and Bisq 4:
[X] Domain name service
[X] TLS certs
[X] Nginx proxy
[X] Basic 11ty site
[ ] Basic http API
[ ] Haveno-reto data
[ ] Bisq data
[ ] Coingecko data
[ ] Forex data
[ ] API
[ ] ... ⌘ [Read more](https://monero.observer/ki9-starts-work-xmr-price-api-data-haveno-bisq/)@prologic@twtxt.net I like the, allegedly, original:
“It can scarcely be denied that the supreme goal of all theory is to make the irreducible basic elements as simple and as few as possible without having to surrender the adequate representation of a single datum of experience.”
Not as simple as the interpretation you used, yet often context is king (or queen).
(#2024-09-24T12:39:32Z) @prologic@twtxt.net It might be simple for you to run echo -e "\t\t" | sha256sum | base64, but for people who are not comfortable in a terminal and got their dev env set up, then that is magic, compared to the simplicity of just copy/pasting what you see in a textfile into another textfile – Basically what @movq@www.uninformativ.de also said. I’m also on team extreme minimalism, otherwise we could just use mastodon etc. Replacing line-breaks with a tab would also make it easier to handwrite your twtxt. You don’t have to hardwrite it, but at least you should have the option to. Just as i do with all my HTML and CSS.
#fzf is the new emacs: a tool with a simple purpose that has evolved to include an #email client. https://sr.ht/~rakoo/omail/
I’m being a little silly, of course. fzf doesn’t actually check your email, but it appears to be basically the whole user interface for that mail program, with #mblaze wrangling the emails.
I’ve been thinking about how I handle my email, and am tempted to make something similar. (When I originally saw this linked the author was presenting it as an example tweaked to their own needs, encouraging people to make their own.)
This approach could surely also be combined with #jenny, taking the place of (neo)mutt. For example mblaze’s mthread tool presents a threaded discussion with indentation.
@xuu@txt.sour.is I think it is more tricky than that.
“A company or entity …”
Also, as I understand it, “personal or household activity” (as you called it) is rather strict: An example could be you uploading photos to a webspace behind HTTP basic auth and sending that link to a friend. So, yes, a webserver is involved and you process your friend’s data (e.g., when did he access your files), but it’s just between you and him. But if you were to publish these photos publicly on a webserver that anyone can access, then it’s a different story – even though you could say that “this is just my personal hobby, not related to any job or money”.
If you operate a public Yarn pod and if you accept registrations from other users, then I’m pretty sure the GDPR applies. 🤔 You process personal data and you don’t really know these people. It’s not a personal/private thing anymore.
I’m bad with faces, I know that. But I’m having a really hard time recognizing Linus in this video:
https://www.youtube.com/watch?v=4WCTGycBceg
Basically a different person to me. Is it just me or has he really changed that much? 😳
i feel like we should isolate a subset of markdown that makes sense and built it into lextwt. it already has support for links and images. maybe basic formatting bold, italic. possibly block quote and bullet lists. no tables or footnotes
i feel like we should isolate a subset of markdown that makes sense and built it into lextwt. it already has support for links and images. maybe basic formatting bold, italic. possibly block quote and bullet lists. no tables or footnotes
@prologic@twtxt.net the basic idea was to stem the hash.. so you have a hash abcdef0123456789... any sub string of that hash after the first 6 will match. so abcdef, abcdef012, abcdef0123456 all match the same. on the case of a collision i think we decided on matching the newest since we archive off older threads anyway. the third rule was about growing the minimum hash size after some threshold of collisions were detected.
@prologic@twtxt.net the basic idea was to stem the hash.. so you have a hash abcdef0123456789... any sub string of that hash after the first 6 will match. so abcdef, abcdef012, abcdef0123456 all match the same. on the case of a collision i think we decided on matching the newest since we archive off older threads anyway. the third rule was about growing the minimum hash size after some threshold of collisions were detected.
So.. basically a rehash of the email “unsend” requests? What if i was to make a (delete: 5vbi2ea) .. would it delete someone elses twt?
So.. basically a rehash of the email “unsend” requests? What if i was to make a (delete: 5vbi2ea) .. would it delete someone elses twt?
So yeah no, whilst it technically works, neither jenny nor yarnd support it very well. Only at a very basic level.
Docker for Web Developers: Getting Started with the Basics
In this post, we’ll discuss Docker for web developers by covering its broad capabilities, strengths, and features for bolstering developer productivity. ⌘ Read more
So this is a great thread. I have been thinking about this too.. and what if we are coming at it from the wrong direction? Identity being tied to a given URL has always been a pain point. If i get a new URL its almost as if i have a new identity because not only am I serving at a new location but all my previous communications are broken because the hashes are all wrong.
What if instead we used this idea of signatures to thread the URLs together into one identity? We keep the URL to Hash in place. Changing that now is basically a no go. But we can create a signature chain that can link identities together. So if i move to a new URL i update the chain hosted by my primary identity to include the new URL. If i have an archived feed that the old URL is now dead, we can point to where it is now hosted and use the current convention of hashing based on the first url:
The signature chain can also be used to rotate to new keys over time. Just sign in a new key or revoke an old one. The prior signatures remain valid within the scope of time the signatures were made and the keys were active.
The signature file can be hosted anywhere as long as it can be fetched by a reasonable protocol. So say we could use a webfinger that directs to the signature file? you have an identity like frank@beans.co that will discover a feed at some URL and a signature chain at another URL. Maybe even include the most recent signing key?
From there the client can auto discover old feeds to link them together into one complete timeline. And the signatures can validate that its all correct.
I like the idea of maybe putting the chain in the feed preamble and keeping the single self contained file.. but wonder if that would cause lots of clutter? The signature chain would be something like a log with what is changing (new key, revoke, add url) and a signature of the change + the previous signature.
# chain: ADDKEY kex14zwrx68cfkg28kjdstvcw4pslazwtgyeueqlg6z7y3f85h29crjsgfmu0w
# sig: BEGIN SALTPACK SIGNED MESSAGE. ...
# chain: ADDURL https://txt.sour.is/user/xuu
# sig: BEGIN SALTPACK SIGNED MESSAGE. ...
# chain: REVKEY kex14zwrx68cfkg28kjdstvcw4pslazwtgyeueqlg6z7y3f85h29crjsgfmu0w
# sig: ...
So this is a great thread. I have been thinking about this too.. and what if we are coming at it from the wrong direction? Identity being tied to a given URL has always been a pain point. If i get a new URL its almost as if i have a new identity because not only am I serving at a new location but all my previous communications are broken because the hashes are all wrong.
What if instead we used this idea of signatures to thread the URLs together into one identity? We keep the URL to Hash in place. Changing that now is basically a no go. But we can create a signature chain that can link identities together. So if i move to a new URL i update the chain hosted by my primary identity to include the new URL. If i have an archived feed that the old URL is now dead, we can point to where it is now hosted and use the current convention of hashing based on the first url:
The signature chain can also be used to rotate to new keys over time. Just sign in a new key or revoke an old one. The prior signatures remain valid within the scope of time the signatures were made and the keys were active.
The signature file can be hosted anywhere as long as it can be fetched by a reasonable protocol. So say we could use a webfinger that directs to the signature file? you have an identity like frank@beans.co that will discover a feed at some URL and a signature chain at another URL. Maybe even include the most recent signing key?
From there the client can auto discover old feeds to link them together into one complete timeline. And the signatures can validate that its all correct.
I like the idea of maybe putting the chain in the feed preamble and keeping the single self contained file.. but wonder if that would cause lots of clutter? The signature chain would be something like a log with what is changing (new key, revoke, add url) and a signature of the change + the previous signature.
# chain: ADDKEY kex14zwrx68cfkg28kjdstvcw4pslazwtgyeueqlg6z7y3f85h29crjsgfmu0w
# sig: BEGIN SALTPACK SIGNED MESSAGE. ...
# chain: ADDURL https://txt.sour.is/user/xuu
# sig: BEGIN SALTPACK SIGNED MESSAGE. ...
# chain: REVKEY kex14zwrx68cfkg28kjdstvcw4pslazwtgyeueqlg6z7y3f85h29crjsgfmu0w
# sig: ...
@aelaraji@aelaraji.com Ahh it might very well be a Clownflare thing as @lyse@lyse.isobeef.org eluded to 🤣 One of these days I’m going to get off Clownflare myself, when I do I’ll share it with you. My idea is to basically have a cheap VPS like @eldersnake@we.loveprivacy.club has and use Wireguard to tunnel out. The VPS becomes the Reverse Proxy that faces the internet. My home network then has in inbound whatsoever.
Current flutter source has been pushed - https://github.com/stig-atle/YarnDesktopClient , flutter source is in main branch. The GTK4 version is in it’s own branch (just wanted to keep a copy of that too).
Keep in mind it’s early version. But it does have the basics implemented.
@bender@twtxt.net haha funny! though i just realized my ISP is the only one with fiber pulled to the property so i would have to get a phone line from them some how. The other ISP in the area is basically a mobile hotspot.
@bender@twtxt.net haha funny! though i just realized my ISP is the only one with fiber pulled to the property so i would have to get a phone line from them some how. The other ISP in the area is basically a mobile hotspot.
receieveFile())? 🤔
he emailed my ISP about causing logging abuse. This is the only real ISP in my area, its gonna basically send me back to dialup.
receieveFile())? 🤔
he emailed my ISP about causing logging abuse. This is the only real ISP in my area, its gonna basically send me back to dialup.
Google Chrome will have Gemini LLM built into the browser.
Google Chrome will have Gemini LLM built into the browser.
I run Plan 9 on my server and my main home workstation (a raspberry pi). My “daily driver” time is basically split between that and a Mac (excluding time on my phone, i suppose). I think it looks elegant, too. :-)
What is Git? Our beginner’s guide to version control
Let’s get you started on your Git journey with basic concepts to know, plus a step-by-step on how to install and configure the most widely used version control system in the world.
The post What is Git? Our beginner’s guide to version control appeared first on The GitHub Blog. ⌘ Read more
How to Hide iPhone Keyboard When It’s Covering Buttons & Won’t Go Away
Some iPhone users may find that the onscreen keyboard occasionally gets stuck on screen and covers buttons or other elements on the the screen, preventing interaction with the iPhone and preventing the dismissal of the iPhone keyboard. This can happen for a variety of reasons, whether in Messages, Whatsapp, Instagram, FaceBook, Mail, and basically any … [Read More](https://osxdaily.com/2024/05/01/fix-iphone … ⌘ Read more
Been clearing out my pod a bit and blocking unwanted domains that are basically either a) just noise and/or b) are just 1-way (whose authors never reply or are otherwise unaware of the larger ecosystem)
Let me know if y’all have any other candidates you’d like me to add to the blocked domain list?
Basically a Portable TESLA Coil! ⌘ Read more
Erlang Solutions: A Guide to RabbitMQ
Looking to learn more about the basics of RabbitMQ? This powerful message broker plays a key role in modern, distributed systems.
This post will break down its fundamentals and highlight its importance in the world of modern, distributed systems.
An introduction to RabbitMQRabbitMQ emerged from the need to create a scalable, robust messaging system that was able to handle high volumes of communications between applications, all while maintaining both data and p … ⌘ Read more
The 2024 trends on cloud computing by Kelsey Hightower and Alex Saroyan
Member post originally published on Netris’s blog Public clouds have basically become identical. Most companies are paying way more for cloud infrastructure than they should. In a nutshell, these statements summarize the key takeaways about the state of cloud computing… ⌘ Read more
对于吉他来说,该如何学习音阶?
明确目标所有的指板理论/指型只是 「工具」,仅仅是帮助我们更好表达内心音乐的 「手段」。想象一下你是萨克斯手、键盘手、歌手、提琴手该如何去solo呢?音乐家表达音乐的 内核手段是一样的,只不过放在了不同的乐器上罢了。
Barrett Tagliarino的《Guitar Fretboard Workbook》说得很好:音阶、琶音、和弦只不过是练习,会让你逐渐无聊烦躁。我们越快掌握这些基础,才能越快开始 演奏真正令人兴奋的音乐!但如果缺乏这些基础,我们在演奏细腻的音乐内容的时候,就容易遇到非常多的令人沮丧的障碍。
_By themselves, scales, chords, and arpeggios are nothing but exercises and will bore you. The sooner you learn these basics, the sooner you will start … ⌘ Read more
Erlang Solutions: gen_statem Unveiled
gen_statem and protocolsThis blog post is a deep dive into some of the concepts discussed in my recent conference talk at FOSDEM. The presentation explored some basic theoretical concepts of Finite State Machines, and some special powers of Erlang’s gen_statem in the context of protocols and event-driven development, and building upon this insi … ⌘ Read more
Erlang Solutions: gen_statem Unveiled
gen_statem and protocolsThis blog post is a deep dive into some of the concepts discussed in my recent conference talk at FOSDEM. The presentation explored some basic theoretical concepts of Finite State Machines, and some special powers of Erlang’s gen_statem in the context of protocols and event-driven development, and building upon this insi … ⌘ Read more
yarn should define its own federation protocol that extends the basic twtxt in ways that twtxt doesn’t allow. it’s time. and i’ve got ideas!
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.
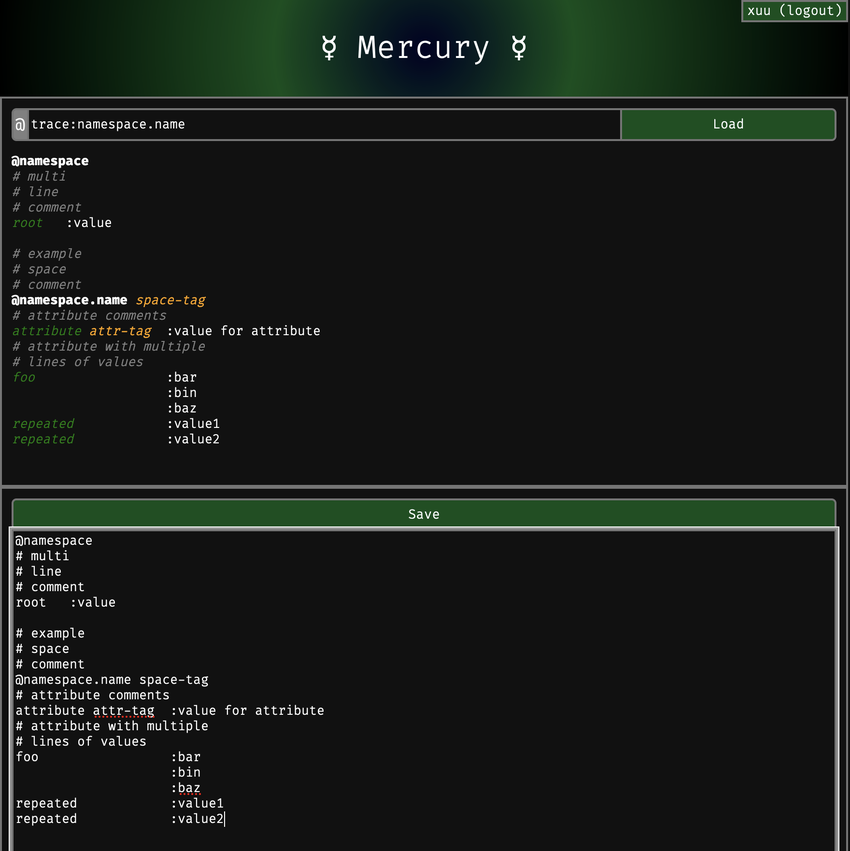
the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.

the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
@movq@www.uninformativ.de Haha! yeah sounds about like my HS CS program. A math teacher taught visual basic and pascal. and over on the other end of the school we had “electronics” which was a room next to the auto body class where they had a bunch of random computer parts scavenged from the district decommissioned surplus storage.
The advanced class would piece together training kits for the basic class to put together.
@movq@www.uninformativ.de Haha! yeah sounds about like my HS CS program. A math teacher taught visual basic and pascal. and over on the other end of the school we had “electronics” which was a room next to the auto body class where they had a bunch of random computer parts scavenged from the district decommissioned surplus storage.
The advanced class would piece together training kits for the basic class to put together.
Asus Expands Tinker Board 3N Series with 3N Plus and 3N Lite Variants
The Tinker Board 3N is a single-board computer built around the Rockchip RK3568 System-on-Chip which was originally launched last year. Asus has expanded this lineup with two new SBC variants, designed to meet diverse requirements, from advanced computing tasks to basic functionalities. These two variants are powered by the Rockchip RK3568 SoC as in the […] ⌘ Read more
Twtxt spec enhancement proposal thread 🧵
Adding attributes to individual twts similar to adding feed attributes in the heading comments.
https://git.mills.io/yarnsocial/go-lextwt/pulls/17
The basic use case would be for multilingual feeds where there is a default language and some twts will be written a different language.
As seen in the wild: https://eapl.mx/twtxt.txt
The attributes are formatted as [key=value]
They can show up in the twt anywhere it is not enclosed by another element such as codeblock or part of a markdown link.
Twtxt spec enhancement proposal thread 🧵
Adding attributes to individual twts similar to adding feed attributes in the heading comments.
https://git.mills.io/yarnsocial/go-lextwt/pulls/17
The basic use case would be for multilingual feeds where there is a default language and some twts will be written a different language.
As seen in the wild: https://eapl.mx/twtxt.txt
The attributes are formatted as [key=value]
They can show up in the twt anywhere it is not enclosed by another element such as codeblock or part of a markdown link.
Amazon Sells Apple Watch Series 9 for $329, Despite Apple Watch Sales Ban Beginning Again
The latest Apple Watch models are apparently facing another sales ban starting tomorrow, due to an ongoing patent dispute with a company named Masimo, according to reports. This basically means that Apple will be temporarily blocked from selling Apple Watch models that have blood oxygen sensors, which includes Series 9 and Ultra 2, though there … [Read More] … ⌘ Read more
Empowering Uruguay’s future workforce with AI
During the second cycle of Git Commit Uruguay, students learned the basics of AI and built their own AI-powered projects.
The post Empowering Uruguay’s future workforce with AI appeared first on The GitHub Blog. ⌘ Read more
** A scrappy fiddle **
I’ve had fun playing at implementing a very basic visual programming system over the last few days. I like the direction I’ve s … ⌘ Read more
How to Stop iPhone Siri Listening to You
Due to the nature of how Hey Siri on iPhone works, Siri is basically always listening to you and your surroundings, if the Hey Siri feature is enabled. This is necessary to hear the “Hey Siri” activation word so that Siri knows to pick up the command you give to it, and the always on … Read More ⌘ Read more
With all M$’s apps being basically fancy web apps, there is no need to actually install any of their legacy applications locally anymore. Since I am online basically 100% of the time this turns my Office experience in a Chromebook like one. No installs, never outdated software. Just a yearly subscription contribution to worry about.
Obligatory Twtxt post: I love how I can simply use a terminal window and some very basic tools (echo, scp, ssh) to publish thoughts, as they pop up, onto the Internet in a structured way, that can be found and perhaps even appreciated.
@prologic@twtxt.net the new product was GPTs. A way to create tailored bots for specific use cases. https://openai.com/blog/introducing-gpts (fun fact: I did an internal hackathon where we made something like this for $work onboarding. And I won a prize!)
The competed project is poe https://quorablog.quora.com/Introducing-creator-monetization-for-Poe which is basically the same idea. Make a AI bot tailored to a specific domain of knowledge. And monitize it.
The timing fits very well as openAI announced it just a few weeks ago.
@prologic@twtxt.net the new product was GPTs. A way to create tailored bots for specific use cases. https://openai.com/blog/introducing-gpts (fun fact: I did an internal hackathon where we made something like this for $work onboarding. And I won a prize!)
The competed project is poe https://quorablog.quora.com/Introducing-creator-monetization-for-Poe which is basically the same idea. Make a AI bot tailored to a specific domain of knowledge. And monitize it.
The timing fits very well as openAI announced it just a few weeks ago.
So now that I have a basic Twtxt form, I can also update my feed even when I am not on my PC.
Anyone else keeping personal .log files updated through basic shell commands?
5 iCloud Security Features You Should Be Using
iCloud is packed full of features that make using devices in the Apple ecosystem super easy and fluid, but there are some security features and capabilities offered by iCloud that literally everyone should be using because of their added benefits to security, convenience, and capabilities. While it’s generally a good idea to basically use every … Read More ⌘ Read more
3 strategies to expand your threat model and secure your supply chain
How to get the security basics right at your organization.
The post 3 strategies to expand your threat model and secure your supply chain appeared first on The GitHub Blog. ⌘ Read more
Video: Does BASIC make programmers “mentally mutilated beyond hope of regeneration”?
Edsger Dijkstra says yes. ⌘ Read more
“The Great Myths of Computer History”, BASIC Week, & Amiga Week
July is gonna be friggin’ awesome. ⌘ Read more
Bloatware removal on Android without Root and without a PC
In this blog post, I want to share an alternative method for removing bloatware from your Android phone without the need for a PC. I discovered most of the apps during my recent adventure of migrating to a new phone. With the help of a few tools and some basic knowledge, you can debloat your phone and easily revert any changes if necessary. ⌘ Read more
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
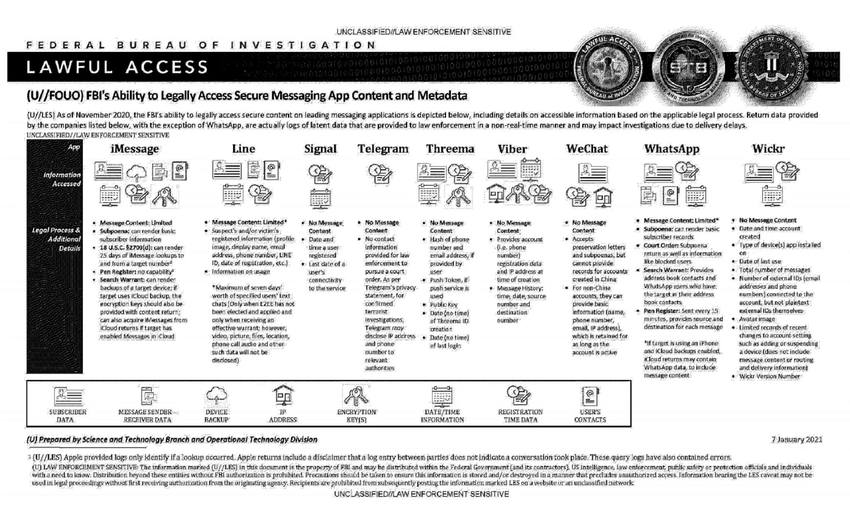
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.

This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
@prologic@twtxt.net The hackathon project that I did recently used openai and embedded the response info into the prompt. So basically i would search for the top 3 most relevant search results to feed into the prompt and the AI would summarize to answer their question.
@prologic@twtxt.net The hackathon project that I did recently used openai and embedded the response info into the prompt. So basically i would search for the top 3 most relevant search results to feed into the prompt and the AI would summarize to answer their question.
CodeQL zero to hero part 2: getting started with CodeQL
Learn the basics of CodeQL and how to use it for security research! In this blog, we will teach you how to leverage GitHub’s static analysis tool CodeQL to write custom CodeQL queries. ⌘ Read more
What is a good device for home virtualization these days? I have been looking at the Intel NUC 13 pro’s. Basically I want something “quiet” (ie not a screaming banshee 1U), smallish, but with lots of threads and rams. Disk will come from an external NAS.
What is a good device for home virtualization these days? I have been looking at the Intel NUC 13 pro’s. Basically I want something “quiet” (ie not a screaming banshee 1U), smallish, but with lots of threads and rams. Disk will come from an external NAS.
twtxt, as I believe it was originally intended, are short little status updates – that’s it.
So, basically a .plan file for finger. But, on the web. like a *web*finger. We have come full circle on this loop!