Docker Desktop 4.21: Support for new Wasm runtimes, Docker Init support for Rust, Docker Scout Dashboard enhancements, Builds view (Beta), and more
Docker Desktop 4.21 is now available, uses less memory, and includes Docker init support for Rust, new Wasm runtimes support, enhancements to Docker Scout dashboards, Builds view (Beta), and performance and filesystem enhancements to Docker Desktop on macOS. ⌘ Read more
@reddit_world_news@feeds.twtxt.net dystopian. get ophones, use lockdown mode.
3D printing a Rocket that uses itself as fuel! #rocket #3dprinting href=”https://txt.sour.is/search?q=%23diy”>#diy** ⌘ Read more
Question to all you Gophers out there: How do you deal with custom errors that include more information and different kinds of matching them?
I started with a simple var ErrPermissionNotAllowed = errors.New("permission not allowed"). In my function I then wrap that using fmt.Errorf("%w: %v", ErrPermissionNotAllowed, failedPermissions). I can match this error using errors.Is(err, ErrPermissionNotAllowed). So far so good.
Now for display purposes I’d also like to access the individual permissions that could not be assigned. Parsing the error message is obviously not an option. So I thought, I create a custom error type, e.g. type PermissionNotAllowedError []Permission and give it some func (e PermissionNotAllowedError) Error() string { return fmt.Sprintf("permission not allowed: %v", e) }. My function would then return this error instead: PermissionNotAllowedError{failedPermissions}
At some layers I don’t care about the exact permissions that failed, but at others I do, at least when accessing them. A custom func (e PermissionNotAllowedError) Is(target err) bool could match both the general ErrPermissionNotAllowed as well as the PermissionNotAllowedError. Same with As(…). For testing purposes the PermissionNotAllowedError would then also try to match the included permissions, so assertions in tests would work nicely. But having two different errors for different matching seems not very elegant at all.
Did you ever encounter this scenario before? How did you address this? Is my thinking flawed?
Introduction to SELinux
SELinux is the most popular Linux Security Module used to isolate and protect system components from one another. Learn about different access control systems and Linux security as I introduce the foundations of a popular type system. ⌘ Read more
Ditching Pocket Premium: Streamline link saving with Telegram
For the past two years, I’ve been using Pocket to save links that I want to revisit later. However, as my yearly subscription is about to expire, I’ve started thinking about finding a free alternative that offers the features I actually use, without paying for unnecessary extras. ⌘ Read more
I could use some healthcare right now, but corporate America sucks. You need to have a full-time job while everyone is being replaced by kiosks.
Ditching Pocket Premium: Streamline link saving with Telegram
For the past two years, I’ve been using Pocket to save links that I want to revisit later. However, as my yearly subscription is about to expire, I’ve started thinking about finding a free alternative that offers the features I actually use, without paying for unnecessary extras. ⌘ Read more
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
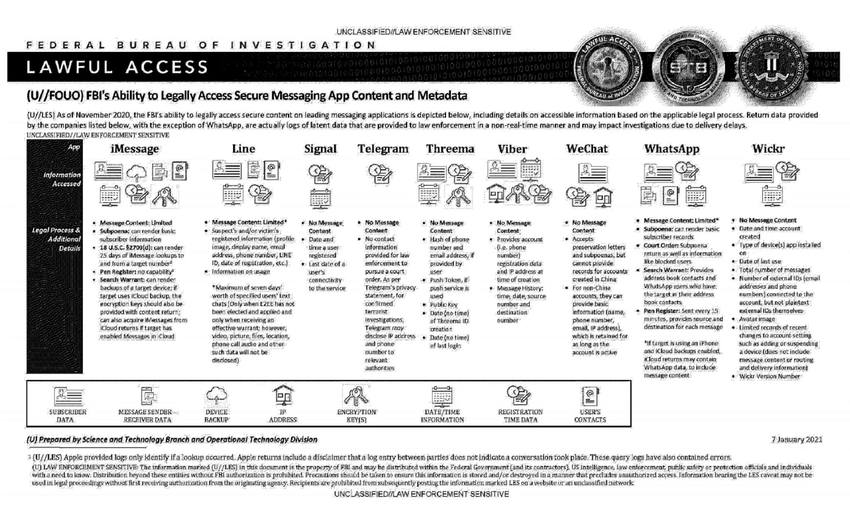
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.

This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
Docker Acquires Mutagen for Continued Investment in Performance and Flexibility of Docker Desktop
I’m excited to announce that Docker, voted the most-used and most-desired tool in Stack Overflow’s 2023 Developer Survey, has acquired Mutagen IO, Inc., the company behind the open source Mutagen file synchronization and networking technologies that enable high-performance remote development. Mutagen’s synchronization and forwarding capabilities facilitate the seamless transfer of code, binary artifacts, and network […] ⌘ Read more
been using the iphone for some days now, and I must say im impressed. I really like it. I will not buy android phone ever again.
** summer’s lease hath all too short a date **
After the excitement of last summer I was hopeful for a chill one this year. So far, so good.
We visited the island where we used to live and started our family. We saw a few friends, and visited some fa … ⌘ Read more
@prologic@twtxt.net ah, but for home use I think it would work well :)
got ny iPhone 14 today, pretty pleased! bur it tales sone time to Get used to.
Erlang Solutions: Unleashing the Power of SNMP: Exposing Your Embedded Elixir/Erlang (Nerves, GRiSP) Apps to the World
Did you know that Erlang/OTP ships with built-in SNMP (Simple Network Management Protocol) support? Using SNMP is a great way to integrate your Elixir or Erlang application into an industrial environment. This will be of particular interest for those working with embedded … ⌘ Read more
Bridging code and community
Explore the impact of non-code contributions—and why they are often undervalued, the challenges of using open source in regulated environments, and the art of managing projects at the scale of Kubernetes, now on The ReadME Podcast. ⌘ Read more
We Thank the Stack Overflow Community for Ranking Docker the #1 Most-Used Developer Tool
Stack Overflow’s annual 2023 Developer Survey engaged nearly 80,000 developers to learn about their work, the technologies they use, their likes and dislikes, and much, much more. As a company obsessed with serving developers, we’re honored that Stack Overflow’s community ranked Docker the #1 most-desired and #1 most-used developer tool. Since our inclusion in the […] ⌘ Read more
@lyse@lyse.isobeef.org Thanks! It was really nice! They had a great time! And it was warm, but we filled the pool we have at our terrace, and they got to hang out there.
Her actual birthday is tomorrow, so I’m really looking forward to celebrate it! She will get the gift from us that she really wanted so that’ll be nice!
How to use GitHub Copilot: Prompts, tips, and use cases
In this prompt guide for GitHub Copilot, two GitHub developer advocates, Rizel and Michelle, will share examples and best practices for communicating your desired results to the AI pair programmer. ⌘ Read more
@prologic@twtxt.net The hackathon project that I did recently used openai and embedded the response info into the prompt. So basically i would search for the top 3 most relevant search results to feed into the prompt and the AI would summarize to answer their question.
@prologic@twtxt.net The hackathon project that I did recently used openai and embedded the response info into the prompt. So basically i would search for the top 3 most relevant search results to feed into the prompt and the AI would summarize to answer their question.
Home | Tabby This is actually pretty cool and useful. Just tried this on my Mac locally of course and it seems to have quite good utility. What would be interesting for me would be to train it on my code and many projects 😅
Hope you all are doing well! we’re enjoying the heatwave that has hit us. :)
If everybody contemplates the infinite instead of fixing the drains, many of us will die of cholera Helpful context for thinking about AI
CodeQL zero to hero part 2: getting started with CodeQL
Learn the basics of CodeQL and how to use it for security research! In this blog, we will teach you how to leverage GitHub’s static analysis tool CodeQL to write custom CodeQL queries. ⌘ Read more
Erlang Solutions: Lifting Your Loads for Maintainable Elixir Applications
This post will discuss one particular aspect of designing Elixir applications using the Ecto library: separating data loading from using the data which is loaded. I will lay out the situations and present some solutions, including a new library called ecto_require_associations.
Applications will differ, but let’s look at [this example]( … ⌘ Read more
Erlang Solutions: Lifting Your Loads for Maintainable Elixir Applications
This post will discuss one particular aspect of designing Elixir applications using the Ecto library: separating data loading from using the data which is loaded. I will lay out the situations and present some solutions, including a new library called ecto_require_associations.
Applications will differ, but let’s look at [this example]( … ⌘ Read more
The resources I used to pass the DVA-C02 exam
I recently passed my first AWS certification exam and am now an AWS Certified Developer Associate. I want to quickly share the resources I used to prepare. ⌘ Read more
wanted to use my oculus to do some flightsimming on Friday, but now Meta forces you over to facebook. super annoying message that constantly pops up in the desktop client, but then after 10 minutes of flying they show the same message in fullscreen inside the VR glasses. so fuck them. I will try and get it to work on linux instead one day soon when I have time.
JMP: JMP is Launched and Out of Beta
JMP has been in beta for over six years, and today we are finally launching! With feedback and testing from thousands of users, our team has made improvements to billing, phone network compatibility, and also helped develop the Cheogram Android app which provides a smooth onboarding process, good Android integration, and phone-like UX for users of that platform. There is still a long road ahead of us, but with so much behind us we’re comfortable saying JMP is ready for la … ⌘ Read more
Unlock Docker Desktop Real-Time Insights with the Grafana Docker Extension
Explore the benefits of using the Grafana Cloud Docker Extension with Docker Desktop for enhanced observability. ⌘ Read more
Iceberg
 ⌘ Read more
⌘ Read more
@abucci@anthony.buc.ci I think the problem is that NATO does not want to get directly involved, because that scales up everything.
So they provide with the things they can to help instead. It worries me a bit (even though I live in the South of Norway - and Russia borders in the north), but it helps a lot that we have Sweden and Finland next to us. But if shit hits the fan - then it won’t be easy to get anywhere from here, unless we steal a boat and go to England or something like that (or get on a plane).
I try not to worry, but it’s in the back of my mind still.. But we have talked about it in my family, and if things happen then we have a plan on what to do first.
The XMPP Standards Foundation: The XMPP Newsletter May 2023
Welcome to the XMPP Newsletter, great to have you here again! This issue covers the month of May 2023.
Many thanks to all our readers and all contributors!
Like this newsletter, many projects and their efforts in the XMPP community are a result of people’s voluntary work. If you are happy with the services and software you may be using, please consider saying thanks or help these projects! Interested in supporting the Newsletter team? Read more [at the … ⌘ Read more
Applying GitOps principles to your operations
Could we use our Git repository as the source of truth for operational tasks, and somehow reconcile changes with our real-world view? ⌘ Read more
@mckinley@twtxt.net I use spideroak backup, and switched from selfhosted nextcloud to proton drive.
@prologic@twtxt.net that would work if it was using shamir’s secret sharing .. although i think its typically 3 of 5 so you get 3, one to the company, and one to the “third party”. so you can recover all you want.. but if the company or 3rd wants to they need one of your 3 to recover.
but still .. if they are providing them then whats the point of trusting they don’t have copies.
@prologic@twtxt.net that would work if it was using shamir’s secret sharing .. although i think its typically 3 of 5 so you get 3, one to the company, and one to the “third party”. so you can recover all you want.. but if the company or 3rd wants to they need one of your 3 to recover.
but still .. if they are providing them then whats the point of trusting they don’t have copies.
@abucci@anthony.buc.ci buuuuut it show when winter!
In the time scale viewed from the planets perspective, the climate has changed many many times.. The issue is whether that change that will inevitability come is hospitable to us meat bags. Or if we are doomed to take part in the next mass extinction event.
@abucci@anthony.buc.ci buuuuut it show when winter!
In the time scale viewed from the planets perspective, the climate has changed many many times.. The issue is whether that change that will inevitability come is hospitable to us meat bags. Or if we are doomed to take part in the next mass extinction event.
Google Bard or BingGPT are actually quite useful to answer simple questions without having to scroll through many pages of clickbait and AI-generated babble blogposts. I’m currently preparing for the AWS exam (I finally signed up!) and Google Bard explained the differences between Cognito User Pools and Cognito Identity Pools in a simple and understandable way. Even with a tabular overview and examples how to use both services. Now my knowledge is refreshed again. 😄 ⌘ Read more
Also, got almost everything I use up and running on NixOS, last thing I need now is a way to develop directly on my source, I think I need to set up one of those development shell files for it, so that I then can work from vscode or kdevelop. Cmake is currently happy, and I tried to install everything on my system, but the ‘nix build’ works fine - but that pulls from remote repo, I want to compile the local edited source as I work on it.
Rooting with root cause: finding a variant of a Project Zero bug
In this blog, I’ll look at CVE-2022-46395, a variant of CVE-2022-36449 (Project Zero issue 2327), and use it to gain arbitrary kernel code execution and root privileges from the untrusted app domain on an Android phone that uses the Arm Mali GPU. I’ll also explain how root cause analysis of CVE-2022-36449 led to the discovery of CVE-2022-46395. ⌘ Read more
Erlang Solutions: Here’s why you should consider investing in RabbitMQ during a recession
Europe and the US are leading the way in the forecasted recession for 2023, due to persistently high inflation and increasing interest rates. With minimal projected GDP growth, modern technologies can play a crucial role in reducing the impact of economic downturns.
As caution looms, it can be tempting to reign in on your investment. Your initial thought is to balance t … ⌘ Read more
How to automate a Microsoft Power Platform deployment using GitHub Actions
Low-code enables developers and non-developers to build custom applications and solutions with less effort. In this blog, we show you how to automate your low-code deployments using GitHub Actions. ⌘ Read more
Are you using lynx?
So, I kinda regret installing NixOS, I had forgotten why I did not use it for c++ stuff last time. But I learned about ‘flakes’ so Im checking into that now to see if I can use that to my advantage to make it easier. So I’ll give it some more time to see if I can learn what I need to build yarn desktop client on it.
Using an Android phone as a desktop replacement (2023 edition)
Because… Why not? ⌘ Read more
Scrollwheel on bluetooth mouse on ipad does not work in goryon. Other then that it works great!
But you can use mouseclick and move the timeline as you do with touch, so its not a big deal.
Crystal Ball
 ⌘ Read more
⌘ Read more
Decided to pick up my ipad again, I have one of those keyboards for it, as well as a bluetooth mouse, RDP to other machine works really well. A bit surprised about how well it works actually. I often use one of my older laptops and remote into my workstation, but this is a much nicer solution. :)
I have not used AI much at all, I have not paid any attention to it. But today I decided to give stablediffusion a test run, I do only have a 1080 card, so it took some tweaking to output 512x256 images, and I must say it works pretty well. I also had to get one of the memory optimized versions. Fun to test.
How I used GitHub Copilot to build a browser extension
Here’s how, in seven steps, I built my first browser extension with GitHub Copilot—and my three major takeaways about learning and pair programming in the age of AI. ⌘ Read more
Navigation and search improvements for accessibility
Discover the accessibility features within our new navigation and code search which make it easier to use for many more people. ⌘ Read more
Unlocking inclusive design: how Primer’s color system is making GitHub.com more inclusive
How Primer’s updated light and dark theme color contrast strategy resolved hundreds of color-contrast-related accessibility issues over one thousand use cases. ⌘ Read more
von Neumann: I came up with this new system that generalizes probability theory to consider convex sets instead of point estimates. I think that I could use this to prove regret bounds…
Bought a used 2020 Leaf EV for the wife.
@prologic@twtxt.net Yeah, we had some discussion about it once it was announced. I said what I felt (And I do love VR - but for flight simulators etc) - but I just knew it would fail.
Especially when they showed the ridiculous screenshots that they where so proud of with the quality of 15 years ago.
And they they pushed it as a place to work or have meetings during the pandemic.. haha.
And they did not even use it themselves in the company.
Metaverse Could Contribute Up To 2.4% of US GDP By 2035, Study Shows
A study commissioned by Meta has found that the metaverse could contribute around 2.4% to U.S. annual GDP by 2035, equating to as much as $760 billion. Reuters reports: The concept of the metaverse includes augmented and virtual reality technologies that allow users to immerse themselves in a virtual world or overlay information digitally on … ⌘ Read more
How we work: inclusive retrospectives for the GitHub Accessibility leadership team
Learn about tools and processes the GitHub Accessibility leadership team uses for retrospectives that fully engage every team member. ⌘ Read more
Commemorative Plaque
![[Below] On this site on May 12th, 2023, I finally learned how to use the masonry bit for my drill.](https://imgs.xkcd.com/comics/commemorative_plaque.png) ⌘ Read more
⌘ Read more
I’ve restarted my home mail server using wildduck.email. No idea why, guess I just needed a thing
Building a Local Application Development Environment for Kubernetes with the Gefyra Docker Extension
Gefyra is an easy-to-use Docker Desktop extension that connects with Kubernetes to improve development workflows and team collaboration. We show how to install and configure Gefyra in this article. ⌘ Read more
❤️ 🎶: The Moments Of Us by MRCH
Today I get a free (used) bike, was nice of them to aak if we needed it. So now Nanook can start running while I bike, that will be great! (And a challenge).
Tapetum Lucidum
 ⌘ Read more
⌘ Read more
One thing I did in another project was to use sqlite that had encryption. I might do that here as well. That would work well for this.
I need to add ‘thread view’ in the Yarn desktop client, I find my self really missing that when I use it. It will make it much easier to follow threads and such.
I deleted my Twitter account a long time ago, but sometimes I still used Nitter to search Twitter or we linked tweets. I decided to stop that and removed Nitter from my home server and added “twitter.com” to the deny list at NextDNS. There are too many reasons to list here. ⌘ Read more
Definition of e
 ⌘ Read more
⌘ Read more
Gonna code a bit tonight. Clean up the image code, then I will rewrite some of the code that uses libcurl, make a more generic function that I use in the calls, instead of many functions. That will be nice.
Erlang Solutions: Re-implement our first blog scrapper with Crawly 0.15.0
It has been almost four years since my first article about scraping with Elixir and Crawly was published. Since then, many changes have occurred, the most significant being Erlang Solution’s blog design update. As a result, the 2019 tutorial is no longer functional.
This situation provided an excellent opportunity to update the original work and re-implement the Crawler using the new version of Cra … ⌘ Read more
IndiePass, Indigenous or whatever it’s called now (for Android) supports unlisted and private posts now! 🎉 Or did it already before and I just did not notice the setting? At least that was a feature I always missed and needed to use frontmatter when creating a new reply for example. Thanks Mark Sutherland! ⌘ Read more
**RT by @mind_booster: 1/3 🚨Recent @POLITICOEurope leak revealed that US & EU officials have agreed to cooperate on measures to turn public opinion against #encryption.
Experts’ statements by @edri & @globalencrypt have called out against this plan
➡️https://edri.org/our-work/eu-us-plan-offensive-to-legitimise-police-access-to-data-civil-society-responds-amid-growing-fears-press-release/
➡️https://www.globalencryption.org/2023/04/statement-on-eu-us-cooperation-against-encryption/**
1/3 🚨Recent [@POLITICOEurope](https … ⌘ Read more
@prologic@twtxt.net They have some markdown support that you can use, but I have not looked into that yet, I might check on that for clickable links in label.
I now just get all the attached links in each post, check for direct links to images, download them and show them as in the screenshot.
Samsung is known for using Apple references in their advertisements. In this ad, they do it again. Kind of funny. 😂 ⌘ Read more
Love the check-ins. Good to see people all over the world using gopherspace.
@carsten@yarn.zn80.net Been thinking about leaving twitter recently, so much drama there. But I have not decided yet. It’s still a bit useful for me for getting my tech related news stuff and things like that, so I cannot get my self to leave yet.
@prologic@twtxt.net The one I actually use for something is Monero. I also mine it (asic resistant, mined with cpu). The others I just put some savings in every month. The whole pyramid scheme thing - I do not think much about honestly. Crypto is here to stay, won’t go away. And for me it’s better then stocks because I know nothing about stocks and such. I do not put much into it. I also had some NFT stuff that I minted - which I sold for 10x the price later on, but honestly - last year I gained as much as I lost, so it evened out to almost 0.
“the secret list of websites”
Chris Coyier wrote a post mentioning a Washington Post article that analyzed which websites Google used to train its AI model. And it seems that both my blog and my website (I think I should merge them one day) are used. ⌘ Read more
@prologic@twtxt.net yeah. Everything else on my taxes are already folled in. For crypto you need to add each and every transaction. The online service I use has api to each major exchange, pulls the data and crunches the numbers for you though. The problems start when you use decentralised exchanges or unsupported wallets etc. Took some hours to sort out on my end. But now I do not have to worry about it. 😀
Had to add all my crypto to my taxes, damn that is a painful process. There are online services that helps with that part, so I use that to help. but I have transactions all over the place, so it takes a lot of time. But now it’s done for this years tax report :)
Tillitis TKey
The Tillitis TKey, which I first wrote about in September last year,
is now available for sale at the the Tillitis webshop.
The TKey is a small bare-bones RISC-V computer in a USB stick form
factor with no persistent storage that measures apps uploaded to it
and derives a deterministic secret every time the same app is started.
You can use it, for instance, as a security token to keep your private
key and do signing operations. Everyt … ⌘ Read more
Announcing GitHub Actions Deployment Protection Rules, now in public beta
Create and share your own deployment protection rules, or use the rules from our great partners, like Datadog, Honeycomb, New Relic, NodeSource, Sentry, and ServiceNow, to control your deployments with more confidence. And the API is open for the community to build their own rules to make GitHub Enterprise Cloud even better. ⌘ Read more
Erlang Solutions: Re-implement our first blog scrapper with Crawly 0.15.0
It has been almost four years since my first article about scraping with Elixir and Crawly was published. Since then, many changes have occurred, the most significant being Erlang Solution’s blog design update. As a result, the 2019 tutorial is no longer functional.
This situation provided an excellent opportunity to update the original work and re-implement the Crawler using the new version of Crawl … ⌘ Read more
ProcessOne: ejabberd 23.04
This new ejabberd 23.04 release includes many improvements and bug fixes, as well as some new features.
- Many SQL database improvements
mod_mamsupport for XEP-0425: Message Moderation
- New
mod_muc_rtbl, Real-Time Block List for MUC rooms
- Binaries useErlang/OTP 25.3, and changes in containers
A more detailed explanatio … ⌘ Read more
Why is Firefox called Firefox?
A story of bullying, and failing to see if a product name is in use before choosing it. ⌘ Read more
ProcessOne: ejabberd 23.04
This new ejabberd 23.04 release includes many improvements and bug fixes, as well as some new features.
- Many SQL database improvements
mod_mamsupport for XEP-0425: Message Moderation
- New
mod_muc_rtbl, Real-Time Block List for MUC rooms
- Binaries useErlang/OTP 25.3, and changes in containers
A more detailed explanatio … ⌘ Read more
We could ask them? But on the counter would bukket or jan6 follow the pure twtxt feeds? Probably not either way… We could use content negotiation as well. text/plain for basic and text/yarn for enhanced.
We could ask them? But on the counter would bukket or jan6 follow the pure twtxt feeds? Probably not either way… We could use content negotiation as well. text/plain for basic and text/yarn for enhanced.
Multi-repository enablement: effortlessly scale code scanning across your repositories
We’ve gotten great feedback on default setup, a simple way to set up code scanning on your repository. Now, you have the ability to use default setup across your organization’s repositories, in just one click. ⌘ Read more
@funbreaker@twtxt.net I have pushed a fix now to git, I now got rid of the error when I use it on my end. I will create a test account on twtxt later tonight (after dinner and all that) if needed. If you test the latest on your end before that - let me know :) And thanks for your patience.
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
💡 Quick ‘n Dirty prototype Yarn.social protocol/spec:
If we were to decide to write a new spec/protocol, what would it look like?
Here’s my rough draft (back of paper napkin idea):
- Feeds are JSON file(s) fetchable by standard HTTP clients over TLS
- WebFinger is used at the root of a user’s domain (or multi-user) lookup. e.g:
prologic@mills.io->https://yarn.mills.io/~prologic.json
- Feeds contain similar metadata that we’re familiar with: Nick, Avatar, Description, etc
- Feed items are signed with a ED25519 private key. That is all “posts” are cryptographically signed.
- Feed items continue to use content-addressing, but use the full Blake2b Base64 encoded hash.
- Edited feed items produce an “Edited” item so that clients can easily follow Edits.
- Deleted feed items produced a “Deleted” item so that clients can easily delete cached items.
Sam Whited: Concord and Spring Road Linear Parks
In my earlier review of Rose Garden and Jonquil public parks I mentioned
the Mountain-to-River Trail
(M2R), a mixed-use bicycle
and walking trail that connects the two parks.
The two parks I’m going to review today are also connected by the M2R trail in
addition to the [Concord Road Trail](https://blog.samwhited.com/cate … ⌘ Read more
Given the continued hostility of jam6 and buckket over Yarn’a use of Twtxt (even after several years! 😱) I am continuing to face hard decisions.
I am not sure what to do about this. 🤔 I am quite confident that the hostility and sentiment is not held by all Twtxt users past and present 😢
This is a case of a few upset purists who prefer to mock, shame and behave passive aggressively instead of contributing to a healthy discussion and ecosystem.
I am uncertain what Yarn should do here 😢
@funbreaker@twtxt.net okay, so something goes wrong in the response you get. Hm. I see you use twtxt, ill check against there tomorrow and see if I can find the issue (midnight here now). Also ill work on better error output as well when I find the problem.
Thank you for testing!
@abucci@anthony.buc.ci that is an ironic example. Since the inventor of the seatbelt gave rights to use the technology freely.