Today during class we built a small example showing #random vs. #PerlinNoise
#Processing #Python py5
** Sticker party, November **
Some random thoughts including how the band Imagine Dragons is kinda like Metal for kids; distributing apps, even without involving Apple at all, is deeply annoying on macOS; Pokemon ZA is fun, but I think that I’m a turn-based girlie at heart; my partner has been playing a lot of Tears of the Kingdom lately, it has been a lot of fun for me to watch, and hair-pullingly frustrating for our nearly 10 year old who has strong opinions about the correct order of operations in that game; I wrote, but am cu … ⌘ Read more
@prologic@twtxt.net Let’s go through it one by one. Here’s a wall of text that took me over 1.5 hours to write.
The criticism of AI as untrustworthy is a problem of misapplication, not capability.This section says AI should not be treated as an authority. This is actually just what I said, except the AI phrased/framed it like it was a counter-argument.
The AI also said that users must develop “AI literacy”, again phrasing/framing it like a counter-argument. Well, that is also just what I said. I said you should treat AI output like a random blog and you should verify the sources, yadda yadda. That is “AI literacy”, isn’t it?
My text went one step further, though: I said that when you take this requirement of “AI literacy” into account, you basically end up with a fancy search engine, with extra overhead that costs time. The AI missed/ignored this in its reply.
Okay, so, the AI also said that you should use AI tools just for drafting and brainstorming. Granted, a very rough draft of something will probably be doable. But then you have to diligently verify every little detail of this draft – okay, fine, a draft is a draft, it’s fine if it contains errors. The thing is, though, that you really must do this verification. And I claim that many people will not do it, because AI outputs look sooooo convincing, they don’t feel like a draft that needs editing.
Can you, as an expert, still use an AI draft as a basis/foundation? Yeah, probably. But here’s the kicker: You did not create that draft. You were not involved in the “thought process” behind it. When you, a human being, make a draft, you often think something like: “Okay, I want to draw a picture of a landscape and there’s going to be a little house, but for now, I’ll just put in a rough sketch of the house and add the details later.” You are aware of what you left out. When the AI did the draft, you are not aware of what’s missing – even more so when every AI output already looks like a final product. For me, personally, this makes it much harder and slower to verify such a draft, and I mentioned this in my text.
Skill Erosion vs. Skill EvolutionYou, @prologic@twtxt.net, also mentioned this in your car tyre example.
In my text, I gave two analogies: The gym analogy and the Google Translate analogy. Your car tyre example falls in the same category, but Gemini’s calculator example is different (and, again, gaslight-y, see below).
What I meant in my text: A person wants to be a programmer. To me, a programmer is a person who writes code, understands code, maintains code, writes documentation, and so on. In your example, a person who changes a car tyre would be a mechanic. Now, if you use AI to write the code and documentation for you, are you still a programmer? If you have no understanding of said code, are you a programmer? A person who does not know how to change a car tyre, is that still a mechanic?
No, you’re something else. You should not be hired as a programmer or a mechanic.
Yes, that is “skill evolution” – which is pretty much my point! But the AI framed it like a counter-argument. It didn’t understand my text.
(But what if that’s our future? What if all programming will look like that in some years? I claim: It’s not possible. If you don’t know how to program, then you don’t know how to read/understand code written by an AI. You are something else, but you’re not a programmer. It might be valid to be something else – but that wasn’t my point, my point was that you’re not a bloody programmer.)
Gemini’s calculator example is garbage, I think. Crunching numbers and doing mathematics (i.e., “complex problem-solving”) are two different things. Just because you now have a calculator, doesn’t mean it’ll free you up to do mathematical proofs or whatever.
What would have worked is this: Let’s say you’re an accountant and you sum up spendings. Without a calculator, this takes a lot of time and is error prone. But when you have one, you can work faster. But once again, there’s a little gaslight-y detail: A calculator is correct. Yes, it could have “bugs” (hello Intel FDIV), but its design actually properly calculates numbers. AI, on the other hand, does not understand a thing (our current AI, that is), it’s just a statistical model. So, this modified example (“accountant with a calculator”) would actually have to be phrased like this: Suppose there’s an accountant and you give her a magic box that spits out the correct result in, what, I don’t know, 70-90% of the time. The accountant couldn’t rely on this box now, could she? She’d either have to double-check everything or accept possibly wrong results. And that is how I feel like when I work with AI tools.
Gemini has no idea that its calculator example doesn’t make sense. It just spits out some generic “argument” that it picked up on some website.
3. The Technical and Legal Perspective (Scraping and Copyright)The AI makes two points here. The first one, I might actually agree with (“bad bot behavior is not the fault of AI itself”).
The second point is, once again, gaslighting, because it is phrased/framed like a counter-argument. It implies that I said something which I didn’t. Like the AI, I said that you would have to adjust the copyright law! At the same time, the AI answer didn’t even question whether it’s okay to break the current law or not. It just said “lol yeah, change the laws”. (I wonder in what way the laws would have to be changed in the AI’s “opinion”, because some of these changes could kill some business opportunities – or the laws would have to have special AI clauses that only benefit the AI techbros. But I digress, that wasn’t part of Gemini’s answer.)
tl;drExcept for one point, I don’t accept any of Gemini’s “criticism”. It didn’t pick up on lots of details, ignored arguments, and I can just instinctively tell that this thing does not understand anything it wrote (which is correct, it’s just a statistical model).
And it framed everything like a counter-argument, while actually repeating what I said. That’s gaslighting: When Alice says “the sky is blue” and Bob replies with “why do you say the sky is purple?!”
But it sure looks convincing, doesn’t it?
Never againThis took so much of my time. I won’t do this again. 😂
@kiwu@twtxt.net hey, not random! How dare you! (with Greta accent, and emphasis). LOL. Old man here doing, well, like old man do. Wait until you are old, and that will give you a better idea. :-P
hi I haven’t been on here in years how are you random old men who like tech 
Random question: does anyone here happen to know anything about retro hacking?
Random musing from a #Python creative coder:
I have this naïve cumbersome thing for dealing with collinear vertices in a polygon (like a vertex in the middle of an edge that doesn’t change the shape of the polygon, and I tried to replace it with some clever #shapely method such as .simplify(…) or .buffer(0) and failed miserably. So I’ll have to keep my home made check-area-every-three-vertices thing for now…
I’m kind of proud of my idea of representing polygons as a set of frozensets of edge vertex pairs because it eliminates all visually equivalent rotations and reverse ordered rotations (that is, if you don’t have pesky collinear vertices).
@lyse@lyse.isobeef.org I give up. Just doesn’t give me a 360° video. 🥴 Maybe I’m just having bad luck with YouTube’s randomized stuff (maybe I’m getting “experiments”, who knows) …
** Strata **
A Counterfeit - a Plated Person -
I would not be -
Whatever strata of Iniquity
My Nature underlie -
Truth is good Health - and Safety, and the Sky.
How meagre, what an Exile - is a Lie,
And Vocal - when we die -
– Emily Dickinson
I made another game! This one pretty much has one single verb:“move.” The game, like most games I make, is a roguelike that relies heavily on probabilities and rng (random number generation).
Each level is … ⌘ Read more
Ni Hao; bīng qílín!
I’m just dropping in, to emphasize my love for ice cream and the Chinese crawler bots, allocating their time and resources, towards scraping my humble website.

To show my gratitude, I’ve even added a random little dog generator to https://thecanine.ueuo.com/sparkle.html so that everyone can pick up their own custom dogFT, on their journey through my site.
Just a random drawing

We finally got a caliper donated for this year’s scout flea market. We didn’t sell it, but kept it ourselves. It will come in very handy every now and then in our material store. For example, I missed having a caliper in the past when sorting our random assortment of screws or measuring the depth of a hole. It’s a wee bit banged up (probably happened during transport) and didn’t come with a box, but the latter is now solved.
The lid and bottom came from a wardrobe back panel I got from a mate, the sides were rocket sticks in their former lives. I found some scrap of felt in our material store and some hinges laying around in the drawers of my own workshop.
Unfortunately, the table saw teared up the plywood veneer fibres badly, even though I put tape around to prevent that. This is the first time it didn’t work. At. All. To cover that up, I painted the box with some decades old tinting paint (price tag says Deutsche Mark, not Euro!) from my paint cabinet. It’s awesome, works absolutely perfectly and doesn’t smell the slightest bit. I reckon, this caliper box is plenty good enough for occasional use at our scout material store.
How you can tell a “review post” on some random website was written by AI?
Ergonomically nicer than its binocular counterpart
How exactly is this a reason to avoid?! 🤦♂️
@prologic@twtxt.net Yeah, it’s difficult, you often don’t get what you’d expect. They also make heavy use of 3rd party libraries. IIUC, for random numbers, they refer to this library. I’ve read many times that the Rust stdlib is intentionally minimalistic (to make it easier to maintain and port and all that).
I’m struggling with this, using 3rd party libs for so many things isn’t really my cup of tea. I’ll probably make my own tiny little “standard library”. It’s silly, but I don’t see any other options. 🤷
More than 40 drink drivers caught each day on average in Queensland
Police have undertaken more than 700,000 breath tests across the state since January, and are on track to conduct more than 2 million tests in a year for the first time since the COVID-19 pandemic. ⌘ Read more
I wanted to port this to Rust as an excercise, but they still have no random number generator in the core library: https://github.com/rust-lang/rust/issues/130703
How to Disable Backtrack on Apple Watch Turning On Automatically
One of the more curious features of Apple Watch is how the Compass Backtrack feature automatically activates and takes over the Apple Watch screen during workouts, seemingly at random, or even every time a “Hiking” workout or sometimes any outdoor workout of any sort is selected or initiated. Given that the vast majority of hikers, … [Read More](https://osxdaily.com/2025/05/30/how-to-disable-backtrack-on- … ⌘ Read more
@bender@twtxt.net There is no aim. Just learning 😅 That way I can actually speak and write with authority when it comes to these LLM(s) a bit more 🤣 Or maybe I just happen to become that random weirdo genius that invents Skynet™ 😂
Where is “Hide My Email” on iPhone & iPad?
The “Hide My Email” feature on iPhone is incredibly useful, allowing you to create random unique email addresses that forward to your real email address inbox. This feature can help protect your privacy by allowing you to sign up for apps or services without sharing your real email address, while enhancing security from phishing attempts, … Read More ⌘ Read more
Where is “Hide My Email” on iPhone & iPad?
The “Hide My Email” feature on iPhone is incredibly useful, allowing you to create random unique email addresses that forward to your real email address inbox. This feature can help protect your privacy by allowing you to sign up for apps or services without sharing your real email address, while enhancing security from phishing attempts, … Read More ⌘ Read more
Over the past few weeks I’ve been experimenting with and doing some deep learning and researching into neutral networks and evolutionary adaptation of them. The thing is I haven’t gotten very far. I’ve been able to build two different approaches so far with limited results. The frustrating part is that these things are so “random” it isn’t even funny. Like I can’t even get a basic ANN + GA to evolve a network that solves the XOR pattern every time with high levels of accuracy. 😞
@lyse@lyse.isobeef.org Nope, this is some random photo. 😅
My icon on here will never not crack me up. It’s so low quality, it feels like a facebook mom meme. Perfect for random corners of the indie web.
Bluetooth 6.1 Update Set to Improve Privacy, Battery Life of iPhone Accessories
The Bluetooth Special Interest Group (SIG) has released Bluetooth 6.1 as part of its new bi-annual update schedule. The update introduces Randomized Resolvable Private Address (RPA), a feature designed to enhance both privacy and power efficiency.
 😅 And increasing the Twt Hash size will ensure that we never run into the chance of collision for ions to come. Chances of a 50% collision with 64 bits / 12 characters is roughly ~12.44B Twts. That ought to be enough! -- I also propose that we modify all our clients and make this change from the 1st July 2025, which will be Yarn.social's 5th birthday and 5 years since I started this whole project and endeavour! 😱 #Twtxt #Update
that said, and reading to @sorenpeter@darch.dk and @andros@twtxt.andros.dev I have new thoughts. I assume that this won’t change anyone’s opinions or priorities, so it makes no harm sharing them.
It’s always tempting to use something that already exists (like X, Masto, Bsky, etc.) rather that building anything through effort and disagreement until reaching to something useful and valuable together. A ‘social service’ is only useful if people is using it.
I’ll add that I haven’t lost interest on the ‘hacky’ part of twtxt about developing tools, protocols, and extensions as a community. It’s the appealing part! It’s a nice hobby to have, shared with random people across the world.
But this is not the right way for me, and makes me feel that I’m unwelcome to propose something different (after watching replies to my previous twt). Feels like “If you don’t agree, you are free to leave, we’ll miss you.” Naah, not cool. I’ve lived that many times before, and nowadays I don’t have enough spare time and energy for a hobby like that.
Let’s see what happens next with the micro-community!
We havet an AI assistant at work, new version came out today “nearby restaurant recommendations” mentioned. Gotta try that!
Ask it where I can get a burger, knowing there’s 3 spots that had it on the menu, AI says there’s none. Ask it to list all the restaurants nearby it can check… it knows 3, of the 10 or so around, but 1/3, even has a burger, on the menu.
Ask it to list the whole menu at restaurant 1: it hallucinates random meals, none of which they had (I ate there).
Restaurant 2 (the one most people go to, so they must have at least tested it with this one): it lists the soup of the day and ¾ meals available. Incomplete, but better than false.
Restaurant 3: it says “food” and gives a general description of food. You have to be fucking kidding me!
“BuT cAnInE, tHe A(G)i ReVoLuTiOn Is NoW”
Barnes: Parallel ./configure
Tavian Barnes takes on\
the tedious process of waiting for configure scripts to run.
I paid good money for my 24 CPU cores, but ./configure can only
manage to use 69% of one of them. As a result, this random project
takes about 13.5× longer to configure the build than it does to
actually do the build.The purpose of a ./configure script is basically to run the
compiler a bunch of times and check which runs succeeded. In this
way it … ⌘ Read more
Weightedrand:Go 權重隨機選擇
weightedrand (github.com/mroth/weightedrand) 是一個 Go 語言實現的權重隨機選擇庫,可以從一個元素列表中以不同的概率選擇一個元素,也就是所謂的加權隨機選擇(weighted random selection)。你可以爲每個元素設置 “權重”(可以理解爲概率的相對值),然後根據這些權重進行隨機選擇。安裝go get github.com/mroth/we ⌘ Read more
was chillin at the park and this random cat pulled up and started rubbing itself on me ⌘ Read more
@bender@twtxt.net This is just a website that cycles through random Youtube channels? 🤔
I Clicked a Random Button in Google Slides — Then Google Paid Me $2,240
The strange trick that exposed a hidden security flaw (and how you can find bugs like this too).
[Continue reading on InfoSec Write-ups »](https://in … ⌘ Read more
@prologic@twtxt.net Since you have to check and double check everything it spits out (without providing sources), I don’t find any of this helpful. It’s like someone’s in the room with you and that person is saying random stuff that might or might not be correct. At best, it might spark some new idea in your head and then you follow that idea the traditional way.
Information published on the internet (or anywhere, for that matter) was never guaranteed to be correct. But at least you had a “frame of reference”: “Ah, I read this information about Linux on a blog that usually posts about Windows, so this one single Linux post might not necessarily be correct.” That is completely lost with LLMs. It’s literally all mushed together. 🤷
One Random Recon, One Real Bounty: The Paytm Story
From countless dead ends to a single Swagger UI payload — the unexpected breakthrough that changed my bug hunting journey forever.
[Continue reading on InfoSec Write-ups »](https://infosecwriteups.com/ghost-paytm-xss-bounty-4f5efe6a643b?source=rss—-7b … ⌘ Read more
@bender@twtxt.neteapl.me@eapl.me just testing this mention, to see which random nick will be picked. Related, I agree, those animations are truly awesome!
hello friends i spent a couple hours today using a random string generator by charm CLI called hotdiva2000 to make a script that 1) generates a static index.html page 2) the page is a prompt generator where all the prompts are from hotdiva2000!!!!!
this makes more sense if you look at it check it out
Too much hanging out with random pups ⌘ Read more
@eapl.me@eapl.me @bender@twtxt.net @prologic@twtxt.net Not including a photo was a stupid move, sorry. There you go:
This particular one is 95mm wide and 185mm high. Fairly compact.
I can only use it figure out distances to other dates and to do some basic calendar math. I’m not able to actually schedule anything. But I grew up with a month calendar like you have there where all appointments of the entire family was recorded.
By far most of my paper use is drawing random stuff on scratch paper during meetings. :-D
iOS 18.4 Adds New Ambient Music Feature
In iOS 18.4, there’s a new Ambient Music option that can be added to Control Center. There are four different sound categories, including Sleep, Chill, Productivity, and Wellbeing.
Each category can be added to Control Center separately, and tapping one plays a random selection of sounds or music from that particular category.
You can’t choose what’s playing from Control Center, but if … ⌘ Read more
echo "Lorem ipsum" | openssl enc -aes-256-cbc -pbkdf2 -iter 100000 -out message.enc -pass file:shared_key.bin
will take the input string from echo to openssl. It then will
trying to implement it quickly, I get the same questions than you
# https://www.php.net/manual/en/function.openssl-pbkdf2.php
$password = $sharedKey;
$salt = openssl_random_pseudo_bytes(16); # What's the salt length ?
$keyLength = 20; # What's the key length here ?
$iterations = 100000;
$generatedKey = openssl_pbkdf2($password, $salt, $keyLength, $iterations, 'sha256');
echo bin2hex($generatedKey)."\n";
echo base64_encode($generatedKey)."\n";
$iv = openssl_random_pseudo_bytes(16); // AES-256-CBC requires 16-byte IV
$cipherText = openssl_encrypt($message, 'aes-256-cbc', $generatedKey, OPENSSL_RAW_DATA, $iv);
return base64_encode($iv . $cipherText);
Touch Bar on Mac Showing “Touch ID to Sign In” or “Touch ID to Autofill” Requests in Safari? Here’s Why
MacBook Pro users with a Touch Bar equipped model may find themselves using Safari and have the Touch Bar constantly show a seemingly random “Touch ID to Autofill” or “Touch ID to Sign In” request, even if they’re using a website or a webpage with no forms, nothing to sign into, and nothing to autofill. … … ⌘ Read more
A random suggestion. You should add a password to your private ssh key. Why? If someone steals your key, they won’t be able to do anything without the password.
You should run: ssh-keygen -p
And remember to make a backup copy of key file. As a developer, it is a one of the most valuable files on your computer.
Interesting where Goryon saves current logged account? Because if i kill app it will logout me :(. Save i noticed with IndiePass but it logout me in random moment (or maybe same after killed)
@doesnm.p.psf.lt@doesnm.p.psf.lt Are you also using https://cabal.chat or just someone else with the same random username?
rose put crack in apt because jesus christ i just find myself mindlessly chanting “apateu apateu” under my breath at the most random times. some brain programming shit
posting from my phone yayyy just downloaded a random tabbed browser off f-droid for this bc my main mobile browser is firefox focus which isn’t great for persisting data
@emmanuel@wald.ovh Btw I already figured out why accessing your web server is slow:
$ host wald.ovh
wald.ovh has address 86.243.228.45
wald.ovh has address 90.19.202.229
wald.ovh has 2 IPv4 addresses, one of which is dead and doesn’t respond.. That’s why accessing your website is so slow as depending on client and browser behaviors one of two things may happen 1) a random IP is chosen and ½ the time the wrong one is picked or 2) both are tried in some random order and ½ the time its slow because the broken one is picked.
If you don’t know what 86.243.228.45 is, or it’s a dead backup server or something, I’d suggest you remove this from the domain record.
(#malf2rq) @movq Too many random IP(s), hundreds of them, many hundreds of QPS. I can only imagine some crawler(s) going crazy out there and not …
@movq @www.uninformativ.de Too many random IP(s), hundreds of them, many hundreds of QPS. I can only imagine some crawler(s) going crazy out there and not respecting anything at all or even remotely being nice. ⌘ Read more
One benefit with bluesky is your username is also a website. And not a clunky URL with slashes and such. I wish twtxt adopted that. I have advocated for webfinger to for twtxt to let us do something like it with usernames. Nostr has something like it
By default the bsky.social urls all redirect to their feeds like: hmpxvt.bsky.social
Many custom urls will redirect to some kind of linktree or just their feed cwebonline.com or la.bonne.petite.sour.is or if you are a major outlet just to your web presence like https://theonion.com or https://netflix.com
Its just good SEO practice
Do all nostr addresses take you to the person if typed into a browser? That is the secret sauce.
No having to go to some random page first. no accounts. no apps to install. just direct to the person.
One benefit with bluesky is your username is also a website. And not a clunky URL with slashes and such. I wish twtxt adopted that. I have advocated for webfinger to for twtxt to let us do something like it with usernames. Nostr has something like it
By default the bsky.social urls all redirect to their feeds like: hmpxvt.bsky.social
Many custom urls will redirect to some kind of linktree or just their feed cwebonline.com or la.bonne.petite.sour.is or if you are a major outlet just to your web presence like https://theonion.com or https://netflix.com
Its just good SEO practice
Do all nostr addresses take you to the person if typed into a browser? That is the secret sauce.
No having to go to some random page first. no accounts. no apps to install. just direct to the person.
Phase Change
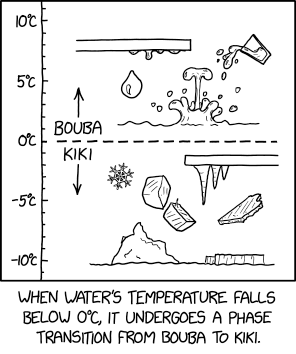 ⌘ Read more
⌘ Read more
Was just catching up on all the LinkedIN garbage that is well umm garbage 🗑️ One was from a candidate I interviewed, so I had to reply to t …
Was just catching up on all the LinkedIN garbage that is well umm garbage 🗑️ One was from a candidate I interviewed, so I had to reply to that 😅 – Anyway…. Saw this random post in my “notifications”:
How do land that job with a Unicorn
First off, you’ll have to define what da fuq a “Unicorn” is! 🤣 My understanding a Unicorn is a mythical creature with … ⌘ Read more
**(#p53b4na) @movq This random comment from another Slashdot article pretry much sums up my view on so-called “AI”:
Elevator music
Tony Isaac …**
@movq @www.uninformativ.de This random comment from another Slashdot article pretry much sums up my view on so-called “AI”:Elevator music
Tony Isaac 20 minutes ago
If you derive your income from producing “elevator music” you might indeed be in danger of losing that income to AI. Also, bumper musi … ⌘ Read more
vtnerd completes 2024 Q3 Monero dev work CCS
vtnerd1 has posted a third and final progress report2 for their full-time 2024/Q3 Monero development work CCS proposal3:
Work overviewThe bulk of the time was making LWS HTTP client requests asynchronous4 - the scanner, exchange rates, and /login are no longer blocked by I/O. [..] I’ve probably missed a few things, this was a somewhat busy month of work.
”`
- LWS /get_random_outs is also now asynchronous
- … ⌘ Read more”`
(#nf6eyeq) @xuu must be extremely unlucky, as it picks a random pod in the peering list 🤣 – Oh but wait… @xuu have you updated recently? @ …
@xuu @txt.sour.is must be extremely unlucky, as it picks a random pod in the peering list 🤣 – Oh but wait… @xuu @txt.sour.is have you updated recently? [@lyse @lyse.isobeef.org](https://twtxt.net/external?uri=https://lyse.isobe … ⌘ Read more
(#fmnhewq) @bender@bender Yeah tell me about it 🤣 I don’t even know why the networking fails at random times to be honest. The CI runner r …
@bender Yeah tell me about it 🤣 I don’t even know why the networking fails at random times to be honest. The CI runner runs in Vultr on a VM connected to the Mills DC via Wireguard VPN. I have no fucking clue why things just fail intermittently at the network level 🤦♂️ ⌘ Read more
Inversion by Aric McBay was another random library pick. Like The Fall of Io, it’s the most recent in a series, though I think this series is pretty loosely connected. In contrast, the villain in this book is simple and cartoonishly evil. The book presents a design for utopia which was interesting but a little cloying. I’m not sure if I’m supposed to want to live there, but I don’t think I do. I enjoyed the book as easy reading, and might try the others in the series some time. (4/4)
I’m enjoying Wesley Chu’s Tao and Io series. Spies, action, ancient aliens. Some funny parts, some interesting world-building parts, some action-filled parts. I picked up The Fall of Io at random from a library a few weeks ago, and it turned out to be the last in a series of six (technically two series), so after finishing that I read the first and am partway through the second. Usually I try to read series in order, but this way is interesting. One thing I liked about The Fall of Io was that it it followed many points of view with somewhat conflicting interests, some more evil than others, and I felt sympathy for most of them. (I was kind of hoping it would be about Jupiter’s moon Io, but it wasn’t, but I’m satisfied with what I ended up with.) (2/4)
m-a-x-c creates Monero churn timing tool
m-a-x-c1 has created Monero Churn Timer 2 - a Python script that generates randomized wait times for XMR transactions and can potentially help users increase their privacy by scheduling churns:
The way it works is as follows: after receiving Monero, you would use the Monero Churn Timer to generate a random wait time. You would then set a reminder to “churn” (i.e., send that transaction to yourself at a new address) after the specified … ⌘ Read more
Fix MacOS Sequoia Network & Wi-Fi Issues with These 6 Tips
Some MacOS Sequoia users have discovered various networking issues with their Mac since installing the MacOS Sequoia 15 system software update. The reported network problems can range from and include random intermittent connection issues with MacOS Sequoia, inability to connect to the internet, unusually slow internet, DNS resolution failures, problems with VPN services, problems with … [Read More](https://osxdaily.com/2024/10/08/f … ⌘ Read more
Recent #fiction #scifi #reading:
The Memory Police by Yōko Ogawa. Lovely writing. Very understated; reminded me of Kazuo Ishiguro. Sort of like Nineteen Eighty-Four but not. (I first heard it recommended in comparison to that work.)
Subcutanean by Aaron Reed; https://subcutanean.textories.com/ . Every copy of the book is different, which is a cool idea. I read two of them (one from the library, actually not different from the other printed copies, and one personalized e-book). I don’t read much horror so managed to be a little creeped out by it, which was fun.
The Wind from Nowhere, a 1962 novel by J. G. Ballard. A random pick from the sci-fi section; I think I picked it up because it made me imagine some weird 4-dimensional effect (“from nowhere” meaning not in a normal direction) but actually (spoiler) it was just about a lot of wind for no reason. The book was moderately entertaining but there was nothing special about it.
Currently reading Scale by Greg Egan and Inversion by Aric McBay.
@prologic@twtxt.net Thanks for writing that up!
I hope it can remain a living document (or sequence of draft revisions) for a good long time while we figure out how this stuff works in practice.
I am not sure how I feel about all this being done at once, vs. letting conventions arise.
For example, even today I could reply to twt abc1234 with “(#abc1234) Edit: …” and I think all you humans would understand it as an edit to (#abc1234). Maybe eventually it would become a common enough convention that clients would start to support it explicitly.
Similarly we could just start using 11-digit hashes. We should iron out whether it’s sha256 or whatever but there’s no need get all the other stuff right at the same time.
I have similar thoughts about how some users could try out location-based replies in a backward-compatible way (append the replyto: stuff after the legacy (#hash) style).
However I recognize that I’m not the one implementing this stuff, and it’s less work to just have everything determined up front.
Misc comments (I haven’t read the whole thing):
Did you mean to make hashes hexadecimal? You lose 11 bits that way compared to base32. I’d suggest gaining 11 bits with base64 instead.
“Clients MUST preserve the original hash” — do you mean they MUST preserve the original twt?
Thanks for phrasing the bit about deletions so neutrally.
I don’t like the MUST in “Clients MUST follow the chain of reply-to references…”. If someone writes a client as a 40-line shell script that requires the user to piece together the threading themselves, IMO we shouldn’t declare the client non-conforming just because they didn’t get to all the bells and whistles.
Similarly I don’t like the MUST for user agents. For one thing, you might want to fetch a feed without revealing your identty. Also, it raises the bar for a minimal implementation (I’m again thinking again of the 40-line shell script).
For “who follows” lists: why must the long, random tokens be only valid for a limited time? Do you have a scenario in mind where they could leak?
Why can’t feeds be served over HTTP/1.0? Again, thinking about simple software. I recently tried implementing HTTP/1.1 and it wasn’t too bad, but 1.0 would have been slightly simpler.
Why get into the nitty-gritty about caching headers? This seems like generic advice for HTTP servers and clients.
I’m a little sad about other protocols being not recommended.
I don’t know how I feel about including markdown. I don’t mind too much that yarn users emit twts full of markdown, but I’m more of a plain text kind of person. Also it adds to the length. I wonder if putting a separate document would make more sense; that would also help with the length.
How to Stop Apple Music from Opening on Mac Randomly
A fair number of Mac users have discovered that the Apple Music application will seemingly spontaneously open itself at random, and even play music, without being prompted to do so. That Apple Music will randomly open itself and even start playing music is highly undesirable behavior for many Mac users, and thus it’s reasonable to … Read More ⌘ Read more
@prologic@twtxt.net Wikipedia claims sha1 is vulnerable to a “chosen-prefix attack”, which I gather means I can write any two twts I like, and then cause them to have the exact same sha1 hash by appending something. I guess a twt ending in random junk might look suspcious, but perhaps the junk could be worked into an image URL like
. If that’s not possible now maybe it will be later.git only uses sha1 because they’re stuck with it: migrating is very hard. There was an effort to move git to sha256 but I don’t know its status. I think there is progress being made with Game Of Trees, a git clone that uses the same on-disk format.
I can’t imagine any benefit to using sha1, except that maybe some very old software might support sha1 but not sha256.
There’s a simple reason all the current hashes end in a or q: the hash is 256 bits, the base32 encoding chops that into groups of 5 bits, and 256 isn’t divisible by 5. The last character of the base32 encoding just has that left-over single bit (256 mod 5 = 1).
So I agree with #3 below, but do you have a source for #1, #2 or #4? I would expect any lack of variability in any part of a hash function’s output would make it more vulnerable to attacks, so designers of hash functions would want to make the whole output vary as much as possible.
Other than the divisible-by-5 thing, my current intuition is it doesn’t matter what part you take.
Hash Structure: Hashes are typically designed so that their outputs have specific statistical properties. The first few characters often have more entropy or variability, meaning they are less likely to have patterns. The last characters may not maintain this randomness, especially if the encoding method has a tendency to produce less varied endings.
Collision Resistance: When using hashes, the goal is to minimize the risk of collisions (different inputs producing the same output). By using the first few characters, you leverage the full distribution of the hash. The last characters may not distribute in the same way, potentially increasing the likelihood of collisions.
Encoding Characteristics: Base32 encoding has a specific structure and padding that might influence the last characters more than the first. If the data being hashed is similar, the last characters may be more similar across different hashes.
Use Cases: In many applications (like generating unique identifiers), the beginning of the hash is often the most informative and varied. Relying on the end might reduce the uniqueness of generated identifiers, especially if a prefix has a specific context or meaning.
Taking the last n characters of a base32 encoded hash instead of the first n can be problematic for several reasons:
Hash Structure: Hashes are typically designed so that their outputs have specific statistical properties. The first few characters often have more entropy or variability, meaning they are less likely to have patterns. The last characters may not maintain this randomness, especially if the encoding method has a tendency to produce less varied endings.
Collision Resistance: When using hashes, the goal is to minimize the risk of collisions (different inputs producing the same output). By using the first few characters, you leverage the full distribution of the hash. The last characters may not distribute in the same way, potentially increasing the likelihood of collisions.
Encoding Characteristics: Base32 encoding has a specific structure and padding that might influence the last characters more than the first. If the data being hashed is similar, the last characters may be more similar across different hashes.
Use Cases: In many applications (like generating unique identifiers), the beginning of the hash is often the most informative and varied. Relying on the end might reduce the uniqueness of generated identifiers, especially if a prefix has a specific context or meaning.
In summary, using the first n characters generally preserves the intended randomness and collision resistance of the hash, making it a safer choice in most cases.
the right way to solve this is to use public/private key(s) where you actually have a public key fingerprint as your feed’s unique identity that never changes.
i would rather it be a random value signed by a key. That way the key can change but the value stays the same.
the right way to solve this is to use public/private key(s) where you actually have a public key fingerprint as your feed’s unique identity that never changes.
i would rather it be a random value signed by a key. That way the key can change but the value stays the same.
Random Apple Pay Charges Affecting iPhone Users in Hungary
Apple Pay is malfunctioning in Hungary, according to reports from several Hungarian news sites. Apple device owners are seeing surprise, unexpected charges without making purchases.
 ⌘ Read more
⌘ Read more
Woman battles back after random road rage shooting
Amari Franklin has loved fashion and design ever since she was a little girl and that love is what helped the Clark Atlanta University senior find her way back, and her calling, after being shot in random road rage attack. ⌘ Read more
@movq@www.uninformativ.de Haha! yeah sounds about like my HS CS program. A math teacher taught visual basic and pascal. and over on the other end of the school we had “electronics” which was a room next to the auto body class where they had a bunch of random computer parts scavenged from the district decommissioned surplus storage.
The advanced class would piece together training kits for the basic class to put together.
@movq@www.uninformativ.de Haha! yeah sounds about like my HS CS program. A math teacher taught visual basic and pascal. and over on the other end of the school we had “electronics” which was a room next to the auto body class where they had a bunch of random computer parts scavenged from the district decommissioned surplus storage.
The advanced class would piece together training kits for the basic class to put together.
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
Trying out a boost format. seems better with text after….
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
Trying out a boost format. seems better with text after….
@eapl.me@eapl.me trying out a boost format.
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
@eapl.me@eapl.me trying out a boost format.
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
Scroll Through Every Mac Desktop & Laptop Ever Made
The Mac turned 40 this week, and if you’re still on an Apple history kick, there’s a fun website that’s worth exploring called Mac40th. Mac40th.com showcases every desktop and portable Mac ever made by Apple in a continuous stream of Macs, displayed in random order. But it’s not just Macs, interspersed with tons of photos, … Read More ⌘ Read more
Ha, this is cool. Has its flaws, although is easy to remember.
An RNG that runs in your brain
Range Safety
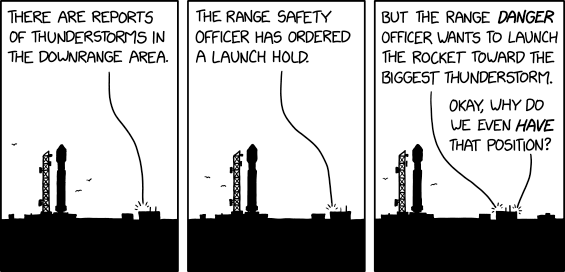 ⌘ Read more
⌘ Read more
True Random Numbers - Computerphile ⌘ Read more
Messages Using High CPU on Mac, Slowing Performance: 6 Troubleshooting Tips
If your Mac feels excessively slow at random, or unreasonably slow for seemingly no apparent reason, you may want to check to see if the Messages app is open, as the Messages app for Mac has been known to use heavy amounts of processor and system resources. Next, you can investigate Activity Monitor for CPU … Read More ⌘ Read more
Hmm when I said “Wireguard is kind of cool” in this twt now I’m not so sure 😢 I can’t get “stable tunnels” to freak’n stay up, survive reboots, survive random disconnections, etc. This is nuts 🤦♂️
I’m curious. How many people truly believe blockchain social networks are the future?
NFTs, tokens, monetization, revenue…
I’m sorry, but how are your random social media blabbers worth any money?
Unless you’re Shakespeare or Einstein or some philosophical or scientific genius, I don’t see why anyone would want to read your posts, let alone cash out some “crypto” from some “wallet”.
And that applies to most people. Sure, your lifestyle and your thoughts may be interesting. But who’s going to start paying to view what’s going on in your life?
As if likes, upvotes, hearts, and subscriptions weren’t narcissistic enough, let’s make people think someone wants to pay them with crypto to view their random posts online.
On my blog: Free Culture Book Club — Jectoons Random Vignettes https://john.colagioia.net/blog/2023/05/13/vignettes.html #freeculture #bookclub
@bender@twtxt.net can you give me your @user for your mastodon? I can then follow you there and see if that part works. I picked some random ones from fosstodon to follow, it said it followed successfully at least.
Biology vs Robotics
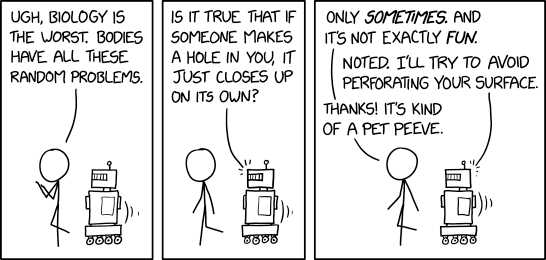 ⌘ Read more
⌘ Read more
I’m honestly thinking about switching browsers, because this “new feature” where Firefox always downloads PDFs first to display them is annoying me so much. I don’t want my Downloads folder to be cluttered with all those random PDFs. If I open a restaurant’s menu PDF, I just want to take a quick look, but don’t want to have the PDF in my Downloads folder until I manually delete it and then delete it from the Recycle Bin again. There are some work-arounds, but no real solution. ⌘ Read more
Blockchain Blasphemy and the Technological Antichrist
There’s a meme YouTube video by Leonardo of Biz ( here) where the villainous Bogs refer to their desire to attain something called “The Akashic Records” using blockchain technology.
This random aside not just shows the attention to detail Leonardo gives what would otherwise be silly videos, but articulates something deep … ⌘ Read more
@eaplmx@twtxt.net This exact thing happened to me last night. I happened to be watching some random Youtube video, then this Ad came on, normally they are short 3-5s ads and I just tolerate them (sometimes) – But this particular ad was 20+ mins long! Somehow I kept listening to it too, despite my daughter telling me I could hit that “Skip Ad” button.
What was it you ask?! 😅 It was one of those testimonial-style, hyped up marketing videos of some product called “Gemini 2” (a currency trading app, allegedly), I kept watching all the way through, it was fantastic! 🤣
Then I went and read up on it! …
Short answer: TOTAL FUCKING SCAM 🤣
Random numbers aren’t truly random!
They’re so predictable! ⌘ Read more
There’s a meme YouTube video by Leonardo of Biz ( here) where the villainous Bogs refer to their desire to attain something called “The Akashic Records” using blockchain technology.
This random aside not just shows the attention to detail Leonardo gives what would otherwise be silly videos, but articulates something deeply troubling about a war unfoldin … ⌘ Read more