[47°09′26″S, 126°43′18″W] Weather forecast alert – storm from NE
On my blog: Toots 🐘 from 09/18 to 09/22 https://john.colagioia.net/blog/2023/09/22/week.html #linkdump #mastodon #socialmedia #week
[47°09′18″S, 126°43′35″W] Dosimeter fixed
Switching from Bitbucket Server and Bamboo to GitHub just got easier
Starting today, GitHub Enterprise Importer supports repository migrations from Bitbucket Server and Bitbucket Data Center, and GitHub Actions Importer offers CI/CD migrations from Bitbucket and Bamboo.
The post Switching from Bitbucket Server and Bamboo to GitHub just got easier appeared first on … ⌘ Read more
On my blog: Developer Diary, World Water Monitoring Day https://john.colagioia.net/blog/2023/09/18/water.html #programming #project #devjournal
Youpi ! La lutte contre “la haine” sur les intertubes continue de plus belle !
Le bruit de fond, léger il y a encore quelques années, devient progressivement plus fort : selon lui, il semble évident que les intertubes, les réseaux sociaux et le web permettent une fois encore aux discours de haine de proliférer. C’est honteux ! C’est bien simple : il ne se passe plus une semaine sans qu’on voie une […] ⌘ Read more
[47°09′36″S, 126°43′18″W] Transfer aborted
[47°09′18″S, 126°43′59″W] Sample analyzing complete – starting transfer
“Talking about Linux Tycoon 3 for Android & Gameboy”
Listen now (18 mins) | Lunduke Journal Podcast Special Announcement ⌘ Read more
[47°09′18″S, 126°43′50″W] Non-significative results – sampling finished
[47°09′06″S, 126°43′18″W] Raw reading: 0x64FEF331, offset +/-2
[47°09′14″S, 126°43′18″W] Sample analyzing complete – starting transfer
[47°09′08″S, 126°43′18″W] Raw reading: 0x64FCC0B1, offset +/-5
[47°09′18″S, 126°43′25″W] Saalmi, retransmit, please
[47°09′23″S, 126°43′18″W] Reading: 1.26 Sv
[47°09′04″S, 126°43′18″W] Dosimeter fixed
[47°09′18″S, 126°43′39″W] Reading: 0.94 Sv
[47°09′18″S, 126°43′29″W] Sample analyzing complete – starting transfer
[47°09′45″S, 126°43′18″W] Waiting for carrier
[47°09′56″S, 126°43′28″W] Reading: 0.18 Sv
On my blog: Toots 🐘 from 08/14 to 08/18 https://john.colagioia.net/blog/2023/08/18/week.html #linkdump #mastodon #socialmedia #week
Oups, l’énergie devient fort chère !
Dès 2022, les choses ont été clairement dites par notre Bruneau De Bercy national : il n’y a pas d’inflation ou, disons plutôt que la France y résiste nettement mieux que le reste de l’Europe. Ou disons plutôt que le gouvernement va agiter frénétiquement ses petits bras musclés pour faire baisser les prix délirants de certains […] ⌘ Read more
[47°09′27″S, 126°43′18″W] 3763 days without news from Herve
[47°09′18″S, 126°43′45″W] Resetting transponder
[47°09′45″S, 126°43′18″W] Transfer 25% complete…
Security alert: social engineering campaign targets technology industry employees
GitHub has identified a low-volume social engineering campaign that targets the personal accounts of employees of technology firms. No GitHub or npm systems were compromised in this campaign. We’re publishing this blog post as a warning for our customers to prevent exploitation by this threat actor. ⌘ Read more
[47°09′18″S, 126°43′44″W] Wind speed: 44kph – batteries low
[47°09′59″S, 126°43′18″W] Resetting transponder
[47°09′18″S, 126°43′10″W] Transfer 25% complete…
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
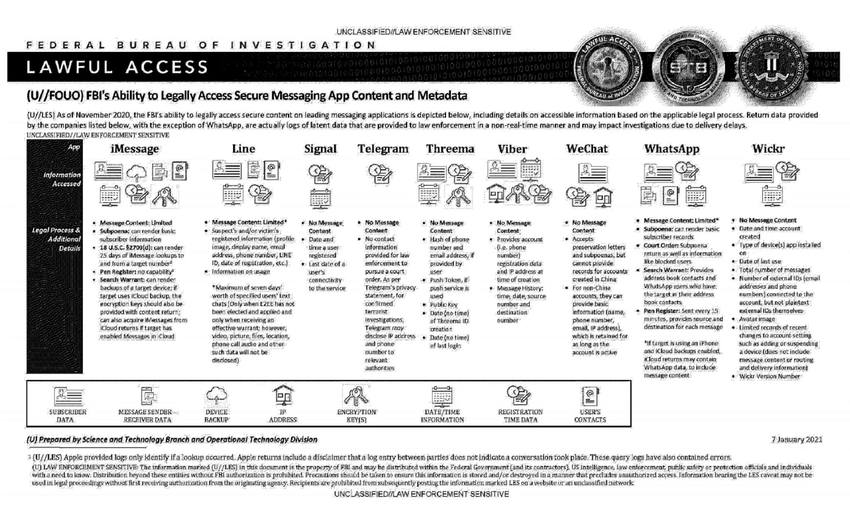
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.

This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
[47°09′18″S, 126°43′24″W] Sample analyzing complete – starting transfer
On my blog: Unraveling Universality https://john.colagioia.net/blog/2023/06/18/universality.html #rant #harm
Echapper à l’inflation : des cryptos et de l’or
La période estivale se rapproche, et elle est généralement propice à la lecture. Cela tombe bien : voici un solide ouvrage qui, en plus de vous occuper pendant vos séances de bronzette à la plage, vous donnera un excellent aperçu de la situation financière actuelle et propose quelques pistes de réflexion pour l’avenir. Dans “Echapper à […] ⌘ Read more
[47°09′18″S, 126°43′29″W] –no signal–
[47°09′18″S, 126°43′50″W] –white noise–
[47°09′18″S, 126°43′15″W] Working impossible due to thunderstorm
[47°09′42″S, 126°43′18″W] Taking samples
On my blog: Real Life in Star Trek, The Survivors https://john.colagioia.net/blog/2023/05/18/survivors.html #scifi #startrek #closereading
9 tips to go from attendee to speaker at a tech conference
Here’s what you need to know to write a compelling session proposal and get on stage. ⌘ Read more
GitHub celebrates developers with disabilities on Global Accessibility Awareness Day
GitHub is the home for all developers and on this Global Accessibility Awareness Day we are thrilled to celebrate the achievements of disabled developers and recent ships that help them build on GitHub. ⌘ Read more
[47°09′35″S, 126°43′18″W] Raw reading: 0x64630DD2, offset +/-2
[47°09′01″S, 126°43′18″W] Waiting for carrier
[47°09′18″S, 126°43′08″W] Transponder malfunction
[47°09′18″S, 126°43′12″W] Dosimeter malfunction
Web Summit Rio 2023: Building an app in 18 minutes with GitHub Copilot X
GitHub CEO Thomas Domke demonstrated the power of GitHub Copilot X live on stage. ⌘ Read more
[47°09′47″S, 126°43′18″W] Resetting dosimeter
Mozilla, OSI, & the memory-holing of Computer History
Listen now (23 min) | The Lunduke Journal of Technology Podcast - April 18, 2023 ⌘ Read more
GitHub joins industry commitment to curb cyber mercenaries
GitHub is proud to join 40 companies endorsing the Cybersecurity Tech Accord principles limiting offensive operations in cyberspace. ⌘ Read more
RT by @mind_booster: The Mousetrap 70th Anniversary Edition #Books #AgathaChristie https://paulasimoesblog.wordpress.com/2023/04/18/the-mousetrap-70th-anniversary-edition-books-agathachristie/
The Mousetrap 70th Anniversary Edition #Books #AgathaChristie paulasimoesblog.wordpress.co…
, para fazerem um aquecimento podem participar no workshop desta tarde das 14h às 18h via meet. Basta que nos enviem um email para: sofia.matias@wikimedia.pt @EurovisionsConf @antena1rtp @nova_fcsh href=”https://txt.sour.is/search?q=%23wikilovesmusicaportuguesa”>#wikilovesmusicaportuguesa**
Este encontro vai ser no próximo sábado (18 Março), para fazerem um aquecimento podem participar no workshop desta tarde das 14h às 18h via meet. Basta que nos enviem um email para: sofia.matias@wikimedia.pt [@Eurovis … ⌘ Read more
[47°09′18″S, 126°43′14″W] Automatic systems disengaged due to blizzard
[47°09′38″S, 126°43′38″W] Reading: 0.18 Sv
**RT by @mind_booster: [Workshop de Introdução ao Git]
📆 06/03
🕘 18 horas
📍 DETI - 4.1.19
A AETTUA em conjunto com o GLUA organizou um workshop de Introdução ao Git onde terás a oportunidade de ficar a conhecer esta plataforma e pôr alguns conceitos em prática.
Inscrições: https://workshop-git.aettua.pt/**
[Workshop de Introdução ao Git]
📆 06/03
🕘 18 horas
📍 DETI - 4.1.19
A AETTUA em conjunto com o GLUA organizou um workshop de Introdução ao Git onde terás a oportunidade de ficar a conhecer esta plataforma e pôr … ⌘ Read more
[47°09′18″S, 126°43′23″W] Dosimeter malfunction
[47°09′29″S, 126°43′18″W] Reading: 0.88 Sv
18:09 ICE
[47°09′05″S, 126°43′18″W] Waiting for carrier
**RT by @mind_booster: Número 6 da #ColecçãoVampiro Os Crimes do Bispo #Livros #Leituras #Policiais
https://paulasimoesblog.wordpress.com/2023/02/18/numero-6-da-coleccaovampiro-os-crimes-do-bispo-livros/**
Número 6 da #ColecçãoVampiro Os Crimes do Bispo #Livros #Leituras #Policiais
[paulasimoesblog.wordpress.co…](https://paulasimoesbl … ⌘ Read more
** Moon maker **
I recently re-read Peter Naur’s“Programming as theory building”. Afterwards I set out to write my own text editor. The paper posits that it’s really hard, if not impossible, to fully communicate about a program and sort of gestures at the futility of documentation…what spun around inside my head as I read was that our primary programming medium — text files — is silly. Like, some folks would totally 100% s … ⌘ Read more
On my blog: Free Culture Book Club — Life Blood, chapters 23 – 25 https://john.colagioia.net/blog/2023/02/18/life-blood-8.html #freeculture #bookclub
386BSD hates me (& NetBSD does too)
Listen now (18 min) | The Lunduke Journal of Technology Podcast - Feb 15, 2023 ⌘ Read more
[47°09′18″S, 126°43′55″W] Dosimeter malfunction
[47°09′39″S, 126°43′18″W] Waiting for carrier
[47°09′40″S, 126°43′18″W] Dosimeter malfunction
[47°09′18″S, 126°43′07″W] Transfer 50% complete…
[47°09′18″S, 126°43′39″W] Non-significative results – sampling finished
I posted about GoToSocial, but another Mastodon-alternative and Fediverse software, Takahē, seems to make fast progress and has some unique features like support for multiple domains or multiple identities per user. I haven’t tried running it yet, but it looks promising! ⌘ Read more
Ce “complot” qui a eu lieu
Avec les #TwittersFiles, ces révélations en chaîne parues sur le réseau social de Musk, il devient évident que sont maintenant avérées ces théories poussées par ce que les médias appellent encore des “complotistes”, et petit à petit, on se rend compte qu’il existe bien un mouvement global, décidé par une petite élite, qui vise à […] ⌘ Read more
RT by @mind_booster: O prazo de inscrição no Youth Hacking 4 Freedom, foi alargado até ao final de Janeiro. Para participarem têm de ter entre 14 e 18 anos e viver na Europa. @fsfe #YH4F #SoftwareFreedom #softwarelivre @ANSOL #wikidata #wikimedia
https://fsfe.org/activities/yh4f/
O prazo de inscrição no Youth Hacking 4 Freedom, foi alargado até ao final de Janeiro. Para participarem têm de ter entre 14 e 18 anos e viver na Europa. @fsfe [#YH4F](htt … ⌘ Read more
[47°09′18″S, 126°43′58″W] Transponder still failing – switching to analog communication
[47°09′36″S, 126°43′18″W] Analyzing samples
[47°09′18″S, 126°43′56″W] Dosimeter overflow
I have a question: Is there something similar to Telegram channels in Matrix? What should I do when I want to enable people to be notified about new blog posts using Matrix? ⌘ Read more
La trêve des complotisseurs
Les températures descendent, le givre s’installe la nuit tombée, les écharpes et – surtout ! – les cols roulés sont de sortie : pas de doute, la période hivernale est là. Et à l’horizon, alors que tintinnabulent clochettes et hommes politiques au crâne vide, on distingue mille et une lumière colorée disposée là par des mairies […] ⌘ Read more
/g/ tomo/os r19344 ⌘ Read more
[47°09′18″S, 126°43′46″W] Taking samples
Social media should be forbidden before 18.
A Smalltalk SmartPhone: The “SqueakPhone”
Watch now (18 min) | An alternate universe of what a smartphone OS could be like. ⌘ Read more
[47°09′01″S, 126°43′18″W] Reading: 0.89000 PPM
[47°09′42″S, 126°43′18″W] Analyzing samples
Derrière la débâcle de FTX, d’étranges coïncidences
Catastrophe dans le monde des cryptomonnaies : FTX, la deuxième plateforme d’échange, s’est effondrée avec fracas la semaine dernière, entraînant avec elle la chute de la valorisation de la plupart des monnaies numériques, Bitcoin compris. Mais à mesure que la poussière retombe, on s’aperçoit que la plateforme ne se contentait pas d’organiser des marchés entre cryptomonnaies : […] ⌘ Read more
[47°09′18″S, 126°43′52″W] Sample analyzing complete – starting transfer