Security alert: Attack campaign involving stolen OAuth user tokens issued to two third-party integrators
On April 12, GitHub Security began an investigation that uncovered evidence that an attacker abused stolen OAuth user tokens issued to two third-party OAuth integrators, Heroku and Travis-CI, to download data from dozens of organizations, including npm. Read on to learn more about the impact to GitHub, npm, and our users. ⌘ Read more
How to secure your end-to-end supply chain on GitHub
Securing your projects is no easy task, but end-to-end supply chain security is more top of mind than ever. We’ve seen bad actors expand their focus to taking over user accounts, commonly used dependencies, and also build systems. Defending against these attacks is hard, because there’s no one thing you can do to protect your […] ⌘ Read more
Spacecraft Debris Odds Ratio
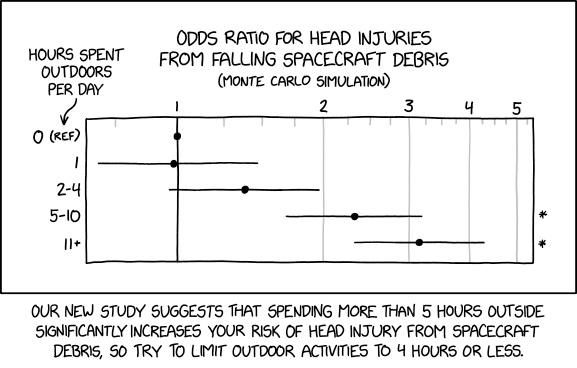 ⌘ Read more
⌘ Read more
not the best move on the side of the red cross to call me and tell me it’s because of my blood donation — i nearly had a panic attack for the 10 seconds that they didn’t tell me it was all fine (why would you call me then‽ and why speak as if you’re going to tell me i’ll be dead in a month‽)
Vulnerability Alert: Avoiding “Dirty Pipe” CVE-2022-0847 on Docker Engine and Docker Desktop
You might have heard about a new Linux vulnerability that was released last week, CVE-2022-0847, aka “Dirty Pipe”. This vulnerability overwrites supposedly read-only files in the Linux kernel host, which could enable attackers to modify files inside the host images from the container instance. If you use Docker Engine natively, we recommend you should update … ⌘ Read more
Conservative leadership race turns nasty between Poilievre and Brown
Encoding and escaping untrusted data to prevent injection attacks
Practical tips on how to apply OWASP Top 10 Proactive Control C4. ⌘ Read more
My public VPS is now only accessible via SSH from my tailnet. One more possible attack vector less. ⌘ Read more
friendlyjordies Attacks Labor ⌘ Read more
Securing the Software Supply Chain with Docker Business
Organizations are increasingly facing new challenges in trying to protect their software supply chain. This has become especially difficult as the workforce has transitioned to a more distributed model with organizations scaling and onboarding more developers on distributed teams. With the number of software supply-chain attacks increasing by 650% in 2021, coordinating all of these […]
The post [Securing the Software Su … ⌘ Read more
Just reading in-depth and trying to understand the security model of Delta.Chat a bit more… There’s a few things that really concern me about how Delta.Chat which relies on Autocrypt work:
- There is no Perfect Forward Secrecy
- No verification of keys
- Is therefore susceptible to Man-in-the-Middle attacks
- Is therefore susceptible to Man-in-the-Middle attacks
- Metadata is a BIG problem with Delta.Chat:
- The
ToandFromandDateare trackable by your Mail provider (amongst many other headers)
- The
Hmmm 🤔 cc @deebs@twtxt.net
Notary v2 Project Update
Supply chain security is something that has been increasingly important to all of us in the last few years. Almost as important as the global supply chains that are having problems distributing goods around the world! There have been many attacks via the supply chain. This is where some piece of software that you use […]
The post Notary v2 Project Update appeared first on Docker Blog. ⌘ Read more
Docker is Updating and Extending Our Product Subscriptions
Docker is used by millions of developers to build, share, and run any app, anywhere, and 55% of professional developers use Docker every day at work. In these work environments, the increase in outside attacks on software supply chains is accelerating developer demand for Docker’s trusted content, including Docker Official Images and Docker Verified Publisher […]
The post [Docker is Updating and Extending Our Product Subscriptions](https:/ … ⌘ Read more
just to make clear: people who actually identify as attack helicopters are unironically valid
Building a healthy and secure software supply chain
Securing the software supply chain is now an everyday concern for developers. As attackers increasingly target open-source components as a way to compromise the software supply chain, developers hold the keys to making their projects as secure as they can be. That’s why Docker continues to invest heavily in our developer tools like Docker Desktop […]
The post [Building a healthy and secure software supply chain](https://www.d … ⌘ Read more
Avoiding npm substitution attacks ⌘ Read more…
I just love seeing IPs being banned after trying to attack my server. It feels really good. Take that bad Russian hackers !
#now-playing ‘Flying Saucer Attack’ by Flying Saucer Attack https://flyingsaucerattack.bandcamp.com/album/flying-saucer-attack-aka-rural-pyschedelia
Metcalf sniper attack - Wikipedia https://en.wikipedia.org/wiki/Metcalf_sniper_attack
Attack of the Flying Space Dwarves! | Mysterious Universe https://mysteriousuniverse.org/2019/02/attack-of-the-flying-space-dwarves/
Bad idea of the day: One of those franchise-themed fighting games, except it’s a rap battle. You get dealt a hand of possible lines, with points for internal rhyme and novelty, & multipliers for referencing previous lines & opponent backstory. External rhymes are combo attacks
“Learn to Code”: The Twitter Meme Attacking Media - The Ringer https://www.theringer.com/tech/2019/1/29/18201695/learn-to-code-twitter-abuse-buzzfeed-journalists
The Messy Truth About Infiltrating Computer Supply Chains https://theintercept.com/2019/01/24/computer-supply-chain-attacks/
Bad idea of the day: live your life as though it is a bayesian poisoning attack on the basilisk
Band name of the day: unmasked attacks
If ‘Evil Maid Attack’ doesn’t literally become the name of an anime soon what is the industry even doing? It’s right there.
Band name of the day: vicious attack dolls
You have the right to a wheel. If you do not have a wheel, one will be provided for you. Please use METAL – not ORGANIC – limbs. We disclaim all liability if you use your own limbs during a sonic attack!
Conspiracy theory: the Sonic The Hedgehog franchise is elaborate fanfiction for the Hawkwind track Sonic Attack, from the perspective of the antagonist. The VO in that track is Dr Robotnik.
Hawkwind - Sonic Attack - YouTube https://www.youtube.com/watch?v=LwRvWpsiM2w
Band name of the day: the red-mad attacks
[1801.01944] Audio Adversarial Examples: Targeted Attacks on Speech-to-Text https://arxiv.org/abs/1801.01944
Is the Mill Architecture (https://en.wikipedia.org/wiki/Mill_architecture) immune to the new out-of-order-execution attacks, theoretically?
Dangerous sound? What Americans heard in Cuba attacks https://apnews.com/88bb914f8b284088bce48e54f6736d84?utm_source=nextdraft