Celebrating 1 year of A11y Design Bootcamp: Takeaways and tips
A11y Design Bootcamp is a live educational program that consists of exercises, discussions, and knowledge shares to raise awareness of web accessibility best practices, the role designers play in creating accessible products, and how to advocate for accessibility with cross-functional partners.
The post [Celebrating 1 year of A11y Design Bootcamp: Takeaways and tips](https://github.blog/2024-05-02-celebrating-1- … ⌘ Read more
Empowering accessibility: GitHub’s journey building an in-house Champions program
As part of GitHub’s dedication to accessibility, we expanded our internal accessibility program and scaled up our internal auditing process to help remove or lower barriers for users with disabilities. Then, we empowered employees from various disciplines to drive accessibility efforts within their teams.
The post [Empowering accessibility: GitHub’s journey building an … ⌘ Read more
Qantas says issue that exposed customer data to others has been resolved
The software issue gave customers access to the personal information and accounts of other people. ⌘ Read more
Qantas investigates app issue that has exposed customer data
A glitch has apparently given customers access to the personal information and accounts of other people. ⌘ Read more
Privacy scare as users report Qantas app glitch
The glitch has apparently given customers access to the personal information and accounts of other people. ⌘ Read more
Privacy scare as users report Qantas app glitch
The glitch has apparently given customers access to the personal information and accounts of other people. ⌘ Read more
FinOps for Kubernetes: engineering cost optimization
Community post by Saqib Jan Cloud has given on-demand access to compute resources, but high availability also makes cost a much more dynamic problem to forecast. This reverberates as companies continue to expand their cloud footprints and adopt… ⌘ Read more
What do Blue Underlines on Text Mean in Microsoft Edge?
If you use Microsoft Edge as your web browser, whether for free GPT 4 access or and DALL-E use, for cross-platform syncing, or any other reason, you may have noticed that you will often see blue underlined text when you’re typing within the browser. If you’re like me, you’re probably wondering what on earth the … Read More ⌘ Read more
訪問 Golang 私有函數、方法、類型和變量
本文譯自 Yarden Laifenfeld 的 Accessing Private Functions, Methods, Types and Variables in Go https://medium.com/@yardenlaif/accessing-private-functions-methods-types-and-variables-in-go-951acccc05a6你 ⌘ Read more
How to Use the Latest GPT 4 & DALL-E 3 Free on iPhone & iPad with Copilot
GPT 4 is an extremely advanced large language model with immense AI capabilities, and DALL-E 3 is a wildly impressive AI image generator that creates pictures from text descriptions. Both of these tools are incredibly powerful and impressive, and while you can access them for a fee through the parent company who developed the models, … [Read More](https://osxdaily.com/2024/04/19/how-use-gpt-4-dall-e-3-f … ⌘ Read more
Beta 2 of iOS 17.5, iPadOS 17.5, macOS Sonoma 14.5, Available for Testing
The second beta versions of iOS 17.5, iPadOS 17.5, MacOS Sonoma 14.5, tvOS 17.5, watchOS 10.5, and visionOS 1.2, have been made available by Apple to participants in the beta testing programs for Apple system software. Both developer and public beta testers are able to access the new builds on any enrolled device that is … [Read More](https://osxdaily.com/2024/04/18/beta-2-of-ios-17-5-ipado … ⌘ Read more
How to Use Hover Text on Mac to Magnify On-Screen Text
Hover Text is an interesting macOS accessibility feature that magnifies the text that’s displayed on your screen. This can be any regular text, a menu item, or a button. As the name suggests, when you hover your mouse cursor over the text, macOS will magnify and display a high-resolution zoomed version of the text in … Read More ⌘ Read more
How to Hide the Sidebar in Microsoft Edge
Microsoft Edge is a surprisingly good web browser with some unique capabilities, like direct and easy GPT 4 access, and it has been a fun browser to experiment with as my new default. But, like many Microsoft software products, the appearance can be a little cluttered if you’re accustomed to the more minimalist designs of … Read More ⌘ Read more
Isode: Harrier 4.0 – New Capabilities
Harrier is our Military Messaging client. It provides a modern, secure web UI that supports SMTP, STANAG 4406 and ACP 127. Harrier allows authorised users to access role-based mailboxes and respond as a role within an organisation rather than as an individual.
You can find out more about Harrier here.
** … ⌘ Read moreHow to Use ChatGPT-4 for Free with Microsoft Edge
The Microsoft Edge browser offers perhaps one of the best and easiest ways for an average person to access and use ChatGPT-4 for free, without having to pay for ChatGPT-4 access through OpenAI. Best of all, Edge is available for just about every major platform, including Mac, Windows, Linux, iPhone, iPad, and Android. With the … Read More ⌘ Read more
Fix “warning: unable to access /Users/Name/.config/git/attributes Permission Denied” Errors
If you’re at the command line and perhaps interacting with Homebrew, Git, or similar, you may run into an error message that says something like the following “warning: unable to access /Users/Name/.config/git/attributes” : Permission denied”. This error message sounds more alarming than it is in most cases, but regardless, you likely want to fix … ⌘ Read more
Snikket: Security notice: Snikket not affected by CVE-2024-3094
A security vulnerability was intentionally added to a widely used open-source
project known as ‘xz’. This project is packaged in many operating systems, and
a lot of software depends upon it. The vulnerability has been assigned the
identifier CVE-2024-3094.
Systems with the vulnerable package may allow an attacker to gain unauthorized
access to the system via SSH, if your system’s SSH server was linked to the
affected packages.
Thankfully, the vulne … ⌘ Read more
Create a Resume with Pages on Mac, iPhone, iPad
Creating a resume is one of those tasks that can be stressful, but it does not need to be if you’re in the Apple ecosystem. That’s because your iPhone, iPad, and Mac, all have a readily accessible series of resume templates that you can access. Whether it’s updating a resume into a new format, or … Read More ⌘ Read more
Create a Resume with Pages on Mac, iPhone, iPad
Creating a resume is one of those tasks that can be stressful, but it does not need to be if you’re in the Apple ecosystem. That’s because your iPhone, iPad, and Mac, all have a readily accessible series of resume templates that you can access. Whether it’s updating a resume into a new format, or … Read More ⌘ Read more
Even AI coding machines will need to rotate their access credentials every 90 days.
How Secure are Personal Hotspot Connections from iPhone?
The Personal Hotspot feature on iPhone turns your iPhone cellular connection into a wi-fi hotspot that other nearby devices and computers can use to access the internet. It’s one of those really great features available for iPhone that allows you to work from just about anywhere that you have a cellular connection, and can also … [Read More](https://osxdaily.com/2024/03/23/how-secure-are-personal-hotspot-connections-from- … ⌘ Read more
in the matter of political voice in the US money is speech and therefore companies use their “free speech” to donate and gain access to politicians. Therefore companies are people. Thanks a lot “citizens united”
in the matter of political voice in the US money is speech and therefore companies use their “free speech” to donate and gain access to politicians. Therefore companies are people. Thanks a lot “citizens united”
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.
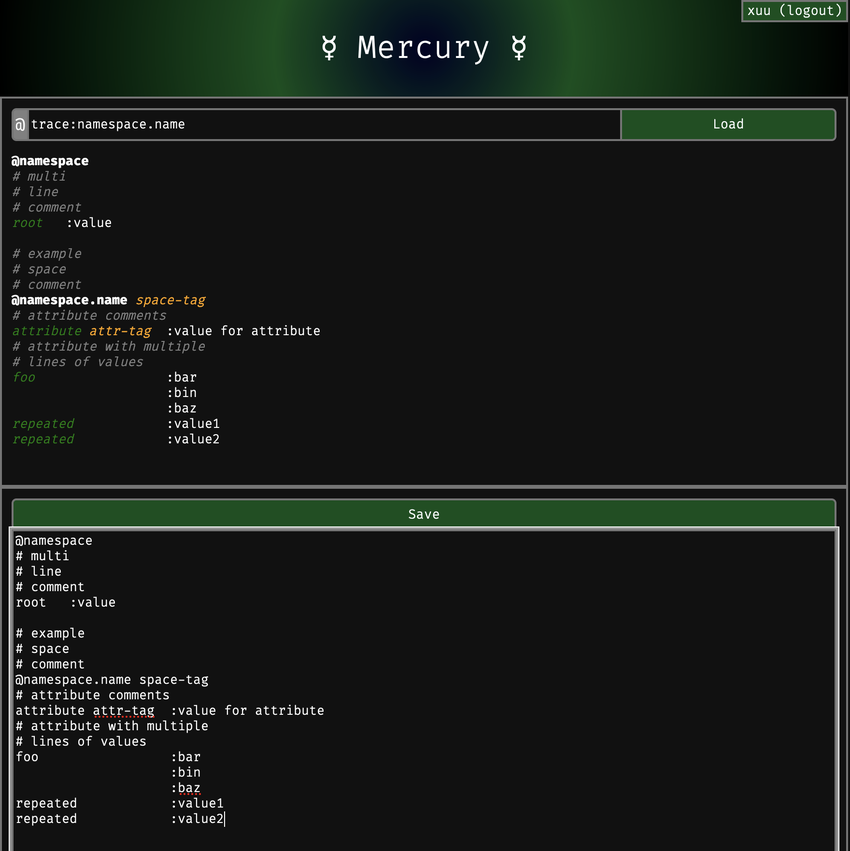
the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
@lyse@lyse.isobeef.org its a hierarchy key value format. I designed it for the network peering tools i use.. I can grant access to different parts of the tree to other users.. kinda like directory permissions. a basic example of the format is:
@namespace
# multi
# line
# comment
root :value
# example space comment
@namespace.name space-tag
# attribute comments
attribute attr-tag :value for attribute
# attribute with multiple
# lines of values
foo :bar
:bin
:baz
repeated :value1
repeated :value2
each @ starts the definition of a namespace kinda like [name] in ini format. It can have comments that show up before. then each attribute is key :value and can have their own # comment lines.
Values can be multi line.. and also repeated..
the namespaces and values can also have little meta data tags added to them.

the service can define webhooks/mqtt topics to be notified when the configs are updated. That way it can deploy the changes out when they are updated.
Huffing product limits part of new bill
A Minnesota family tragedy could prompt a new law to cut down on access materials for huffing. FOX 9 introduced the story of Tommy Byers last August, about ten months after he passed away. Tommy’s mother says her life also ended when her son died from huffing 1, 1-difluoroethane — or DFE. ⌘ Read more
MWC 2024: Microsoft to open up access to its AI models to allow countries to build own AI economies
Tech behemoth Microsoft has unveiled a new set of guiding principles on how it will govern its artificial intelligence (AI) infrastructure, effectively further opening up access to its technology to developers. The announcement came at the Mobile World Congress tech fair in Barcelona on Monday where AI … ⌘ Read more
‘Sweden’s accession to NATO follows that of Finland last year’
2024-02-26 20:40 ‘Sweden’s accession to NATO follows that of Finland last year’ ⌘ Read more
Hungary ratifies Sweden’s NATO accession
Hungary’s parliament approved Sweden’s NATO accession on Monday (February 26), clearing the last hurdle before the historic step by the Nordic country whose neutrality lasted through two world wars and the simmering conflict of the Cold War. Olivia Chan has more. ⌘ Read more
How to Make Microsoft Edge the Default Mac Web Browser
Microsoft Edge is a great web browser alternative that is available for MacOS, iPhone, iPad, and obviously Windows, and Android too. Not only is it fast and offers free access to ChatGPT 4, but if you regularly use different computing platforms, you’ll appreciate that you can sync your browser data across all of your devices, … [Read More](https://osxdaily.com/2024/02/24/how-to-make-microsoft-edge-the-default-mac-web-browser … ⌘ Read more
** In reply to: Scaling accessibility beyond compliance at VA.gov through community and culture - Ad Hoc **
In reply to: Scaling accessibility beyond compliance at VA.gov through community and culture - Ad Hoc
If“accessibility as compliance” is a staircase where outcomes are restricted to the normative limitations of the law, Accessibility Beyond Compliance is an exponential curve. It isn’t limited to fulfilling legal constraints, and we can use it to explore, understand, and b … ⌘ Read more
Empowering all developers to build without barriers
GitHub has been awarded the 2024 Axe Accessibility at Scale Award from Deque Systems. Read more about how we’ve implemented accessibility at scale.
The post Empowering all developers to build without barriers appeared first on The GitHub Blog. ⌘ Read more
Wi-Fi HaLow Development Platform is Compatible with OpenWrt
Morse Micro’s MM6108-EKH03 Wi-Fi HaLow Development Platform offers a sophisticated solution for enhancing wireless connectivity in IoT applications. Ideal for diverse uses like smart city infrastructures, long-range access points, and various industrial and commercial scenarios. The Morse Micro MM6108-EKH03 Wi-Fi HaLow Development Platform provides an efficient configuration for easy and rapid evaluation of Wi-Fi HaLow […] ⌘ Read more
Microchip Launches Affordable PolarFire SoC Kit, Expanding Access to RISC-V and FPGA for Embedded Engineers
Today, Microchip unveiled the PolarFire SoC Discovery Kit, a cost-effective and versatile tool catering to a wide range of users, including students, beginners, and seasoned professionals. This user-friendly kit facilitates quick testing of application ideas, firmware development, programming, and debugging, making it suitable for … ⌘ Read more
GitHub’s Engineering Fundamentals program: How we deliver on availability, security, and accessibility
The Fundamentals program has helped us address tech debt, improve reliability, and enhance observability of our engineering systems.
The post [GitHub’s Engineering Fundamentals program: How we deliver on availability, security, and accessibility](https://github.blog/2024-02-08-githubs-engineering-fundamentals-program-how-we-delive … ⌘ Read more
When Will Space Travel Be Accessible To All? href=”https://txt.sour.is/search?q=%23neildegrassetyson”>#neildegrassetyson** ⌘ Read more
Rotating credentials for GitHub.com and new GHES patches
GitHub received a bug bounty report of a vulnerability that allowed access to the environment variables of a production container. We have patched GitHub.com and rotated all affected credentials. If you have hardcoded or cached a public key owned by GitHub, read on to ensure your systems continue working with the new keys.
The post [Rotating credentials for GitHub.com and new GHES patches](https://github.blog/2024-01-16-ro … ⌘ Read more
Erlang Solutions: Enhancing the Efficiency of Erlang and Elixir System Management: WombatOAM Now Accessible on AWS Marketplace
WombatOAM, a well-established tool for operations and maintenance in both proprietary and open-source Erlang and Elixir systems, is here to simplify your monitoring and management tasks, allowing you to concentrate on your business logic while benefiting from decades of operational expertise in Erlang-based systems. It’s now access … ⌘ Read more
Georg Lukas: Converse.js webchat for prosody-hosted chatrooms
The goal of this post is to make an easily accessible (anonymous)
webchat for any chatrooms hosted on a prosody XMPP
server, using the web client converse.js.
There are two use cases:
Have an easily accessible default support room for users having trouble with
the server or their accounts.Have a working “Join using browser” button on
[search.jabber.network … ⌘ Read more
Cost-efficient $39.90 Travel Router with Dual GbE Ports and Flexible Storage Options
Recently, SeeedStudio introduced the LinkStar-H28K-0408, a compact, pocket-sized router that offers advanced connectivity options. This device is equipped with Dual Gigabit Ethernet ports for high-speed internet access and includes a versatile USB Type-C port with Power Delivery support, enhancing its usability and convenience for various applications. Differing from the LinkS … ⌘ Read more
I appreciate living in a city with a university and multiple libraries nearby. Whenever there is too much noise from construction works at home, I can simply go to the library and enjoy a quiet place. 😌 A 5G cell tower is also within reach, enabling fast internet access without the necessity of logging into the eduroam Wi-Fi network. 🤓 ⌘ Read more
Today, while remotely accessing my home server, I noticed that the network was a bit slower than usual. It turns out, there’s no 5G connection and only an LTE connection with another cell tower more far away. I checked the service provider’s website and there’s actually a problem with a base station nearby. ⌘ Read more
Today, while remotely accessing my home server, I noticed that the network was a bit slower than usual. It turns out, there’s no 5G connection and only an LTE connection with another cell tower more far away. I checked the service provider’s website and there’s actually a problem with a base station nearby. ⌘ Read more
** Accessibility-first **
Whereas mobile-first design and development invited folks to think more expansively about the physical reality of the devices people use, accessibility-first design and development invites folks to think more expansively about the lived experiences, and physical reality of actual people. ⌘ Read more
4 Useful Keyboard Shortcuts Every Mac User Should Know
Want to boost your Mac productivity with some super useful keyboard shortcuts? Here are four of them that every Mac user should know and memorize, where you’re sure to get plenty of use from. From switching between apps, windows, jumping into any directories, or force quitting, read on! Command+Tab Accesses the Application Switcher Hitting Command+Tab … Read More ⌘ Read more
Qnap’s Hybridmount feature makes it possible for me to access the files on OneDrive as if they were available from a local network drive on my Fedora PC. Pretty neat (when everything works).
Ignite Realtime Blog: New Openfire plugin: Reporting Account Affiliations
I’m excited to announce a new Openfire plugin: the Reporting Account Affiliations Plugin!
This plugin implements a new prototype XMPP extension of the same name.
To quote the specification:
In practice, a server may not trust all accounts equally. For example, if a server offers anonymous access or open registration, it … ⌘ Read more
How to Use & Access GPT-4 for Free
You may already be using ChatGPT, the phenomenally powerful and useful AI tool, but the free version is based on GPT-3.5. GPT-4 is said to be ten times more advanced, with enhanced creativity, reliability, up-to-date information, and an ability to interpret more nuanced instructions, so it’s understandable why users would like to explore and experience … Read More ⌘ Read more
How to Use & Access GPT-4 for Free
You may already be using ChatGPT, the phenomenally powerful and useful AI tool, but the free version is based on GPT-3.5. GPT-4 is said to be ten times more advanced, with enhanced creativity, reliability, up-to-date information, and an ability to interpret more nuanced instructions, so it’s understandable why users would like to explore and experience … Read More ⌘ Read more
Having fun with React - yet again. A large part of my job entails (re)learning technologies - luckily I have access to some good resources in the form of training- and tutorial sites, all provided by my employer.
Worked on expanding the scope of accessible alternative press in my RSS aggregator. The numbers reached were 215 media.
Diversity, inclusion, and belonging at GitHub in 2023
We expanded diversity of our employee base, launched several new employee engagement programs, made investments to improve accessibility, and more.
The post Diversity, inclusion, and belonging at GitHub in 2023 appeared first on The GitHub Blog. ⌘ Read more
5 tips for making your GitHub profile page accessible
Your profile’s README invites the world to know you and your work, so it’s important that everyone can read and understand it. In this post, we share some tips for making your README more accessible.
The post 5 tips for making your GitHub profile page accessible appeared first on The GitHub Blog. ⌘ Read more
How to Recover Recently Deleted Passwords on Mac
Forgetting or losing a password is a hassle, but assuming you save your logins and passwords with iCloud Keychain, that happens less and less. But you can still delete a password or login, whether intentionally or accidentally, and then end up needing access to that login information or password later. Fortunately the Mac offers a … Read More ⌘ Read more
Your curated GitHub Universe agenda: AI, ethics, and productivity
Gain actionable insights about the intersection of AI and human skills, while tackling ethics, accessibility, and productivity at these GitHub Universe sessions.
The post Your curated GitHub Universe agenda: AI, ethics, and productivity appeared first on The GitHub Blog. ⌘ Read more
How to “Save As” in MacOS Sonoma & Ventura
Do you wish you had the “Save As” keyboard shortcut back in MacOS Sonoma and MacOS Ventura? Wish no more, it’s easy to re-enable, even in the latest versions of MacOS system software and with the peculiar System Settings experience. Many longtime Mac users adore the “Save As” keyboard shortcut, which had been accessed by … Read More ⌘ Read more
I’m telling ya guys 😅 plex.tv had way better shit™, Get it installed on your own server, get access to free content + your own + whatever and no stupid tracking and bullshit 🤣
Prompting GitHub Copilot Chat to become your personal AI assistant for accessibility
GitHub Copilot Chat can help you learn about accessibility and improve the accessibility of your code. In this blog, we share a sample foundational prompt that instructs GitHub Copilot Chat to become your personal AI assistant for accessibility.
The post [Prompting GitHub Copilot Chat to become your personal AI assistant for accessibility](https://github.blog/2023-10- … ⌘ Read more
Announcing Udemy + Docker Partnership
Docker and Udemy announced a new partnership at DockerCon to give developers a clear, defined, accessible path for learning how to use Docker, best practices, advanced concepts, and everything in between. As the #1 rated online course platform (as ranked by Stack Overflow), Udemy will be the first to house Docker-accredited content and customized learning paths to provide developers with the latest training materials on how to best use Docker tools. ⌘ Read more
How to Install iOS 17 on iPhone
Installing iOS 17 onto your iPhone is easy to do, and you’ll gain access to the neat new features available in iOS 17. This includes everything from customizable contact cards, FaceTime Video voicemail, interactive widgets on your Home Screen, NameDrop easy contact sharing, new stickers features in Messages, new ringtones and text tones, new autocorrect … Read More ⌘ Read more
How I used GitHub Copilot Chat to build a ReactJS gallery prototype
GitHub Copilot Chat can help developers create prototypes, understand code, make UI changes, troubleshoot errors, make code more accessible, and generate unit tests.
The post How I used GitHub Copilot Chat to build a ReactJS gallery prototype appeared first on The GitHub Blog. ⌘ Read more
Changes to How Docker Handles Personal Authentication Tokens
Docker is improving the visibility of Docker Desktop and Hub users’ personal access tokens. Specifically, we are changing how tokens are handled across sessions between the two tools. Learn more about this security improvement. ⌘ Read more
GitHub Copilot Chat beta now available for all individuals
All GitHub Copilot for Individuals users now have access to GitHub Copilot Chat beta, bringing natural language-powered coding to every developer in all languages.
The post GitHub Copilot Chat beta now available for all individuals appeared first on The GitHub Blog. ⌘ Read more
Hardening repositories against credential theft
Some best practices and important defenses to prevent common attacks against GitHub Actions that are enabled by stolen personal access tokens, compromised accounts, or compromised GitHub sessions.
The post Hardening repositories against credential theft appeared first on The GitHub Blog. ⌘ Read more
Docker Desktop 4.22: Resource Saver, Compose ‘include’, and Enhanced RBAC Functionality
Docker Desktop 4.22 is now available, with improved memory & CPU management, support for Compose subprojects, and improvements to role-based access control. ⌘ Read more
GitHub Copilot Chat beta now available for every organization
All GitHub Copilot for Business users now have access to a limited GitHub Copilot Chat beta, bringing the power of conversational coding right to the IDE. ⌘ Read more
Erlang Solutions: How IoT is Revolutionising Supply Chain Management
As global supply chains continue to face significant disruptions, many businesses are turning to IoT to access greater visibility, reactivity, and streamlined operations.
Unforeseen geopolitical conflicts, economic pressures due to inflation and severe climate change events have all contributed to an uncertain and cost … ⌘ Read more
Isode: Icon-PEP 2.0 – New Capabilities
Icon-PEP is used to enable the use of IP applications over HF networks. Using STANAG 5066 Link Layer as an interface.
Listed below are the changes brought in with 2.0.
Web ManagementA web interface is provided which includes:
- Full configuration of Icon-PEP
- TLS (HTTPS) access and configuration including bootstrap with self signed certificate and ide … ⌘ Read more
no wonder he cut off API access and added rate limit.
(De)coding conventions
Navigating the ebb and flow of programming paradigms–from the shifts in the JavaScript ecosystem and TypeScript’s rise, to AI’s role in advancing accessibility, and strategies for encouraging non-code contributions–tune in to the latest episode of The ReadME Podcast for more. ⌘ Read more
Accessibility considerations behind code search and code view
A look at how we improved the readability of code on GitHub. ⌘ Read more
Question to all you Gophers out there: How do you deal with custom errors that include more information and different kinds of matching them?
I started with a simple var ErrPermissionNotAllowed = errors.New("permission not allowed"). In my function I then wrap that using fmt.Errorf("%w: %v", ErrPermissionNotAllowed, failedPermissions). I can match this error using errors.Is(err, ErrPermissionNotAllowed). So far so good.
Now for display purposes I’d also like to access the individual permissions that could not be assigned. Parsing the error message is obviously not an option. So I thought, I create a custom error type, e.g. type PermissionNotAllowedError []Permission and give it some func (e PermissionNotAllowedError) Error() string { return fmt.Sprintf("permission not allowed: %v", e) }. My function would then return this error instead: PermissionNotAllowedError{failedPermissions}
At some layers I don’t care about the exact permissions that failed, but at others I do, at least when accessing them. A custom func (e PermissionNotAllowedError) Is(target err) bool could match both the general ErrPermissionNotAllowed as well as the PermissionNotAllowedError. Same with As(…). For testing purposes the PermissionNotAllowedError would then also try to match the included permissions, so assertions in tests would work nicely. But having two different errors for different matching seems not very elegant at all.
Did you ever encounter this scenario before? How did you address this? Is my thinking flawed?
Introduction to SELinux
SELinux is the most popular Linux Security Module used to isolate and protect system components from one another. Learn about different access control systems and Linux security as I introduce the foundations of a popular type system. ⌘ Read more
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
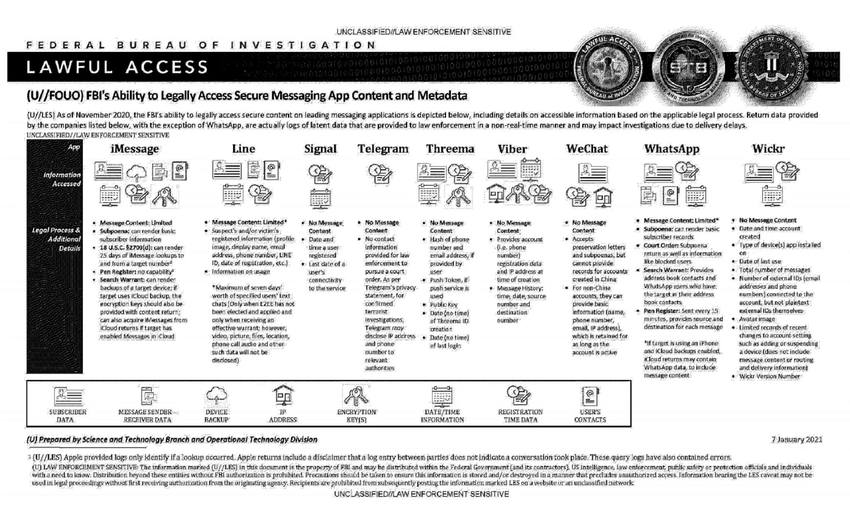
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.

This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
Isode: Harrier 3.3 – New Capabilities
Harrier is our Military Messaging client. It provides a modern, secure web UI that supports SMTP, STANAG 4406 and ACP 127. Harrier allows authorised users to access role-based mailboxes and respond as a role within an organisation rather than as an individual.
![Harrier Inbox view (behind) showing Military Messaging security label and priority parameters; and Message view (in front).](https://www.isode.com/company/wordpress/wp-content/uploads/2023/06/Harrier-M … ⌘ Read more
“give access to repair and maintenance information and spare parts to professional repairers and end-users for at least 7 years after retiring a product […] Software updates will also have to be made available for at least 5 years after retiring a product from the market”
“give access to repair and maintenance information and spare parts to professional repairers and end-users for at least 7 years after retiring a product […] Software updates will also have to be made available for at least 5 years afte … ⌘ Read more
GitHub’s revamped VIP Bug Bounty Program
GitHub’s VIP Bug Bounty Program has been updated to include a clear and accessible criteria for receiving an invitation to the program and more. Learn more about the program and how you can become a Hacktocat, and join our community of researchers who are contributing to GitHub’s security with fun perks and access to staff and beta features! ⌘ Read more
Make your GitHub projects more accessible with accessibility-alt-text-bot
The accessibility-alt-text-bot leaves automated reminders in a comment when a user shares an image without providing meaningful alt text. ⌘ Read more
Erlang Solutions: Sign up for the RabbitMQ Summit Waiting List
Mark your calendars! The Very Early Bird tickets for the RabbitMQ Summit are set to open on 15th June, 2023. In joining the waiting list, you will receive exclusive access to the conference’s best-priced tickets.
This is your chance to secure your spot at the RabbitMQ Summit at a discounted rate, allowing you to make the most of this incredible learning and networking … ⌘ Read more
Heh, I do not regret it anymore, I was able to create a flake.nix file that builds the desktop client on NixOS.
But I now found a bug with keyring access that I need to fix. but the client compiles and starts.
It does not open the keyring - so it hangs and waits and you need to kill it. On my previous machine the keyring got opened at login by another application.
GitHub celebrates developers with disabilities on Global Accessibility Awareness Day
GitHub is the home for all developers and on this Global Accessibility Awareness Day we are thrilled to celebrate the achievements of disabled developers and recent ships that help them build on GitHub. ⌘ Read more
Design’s journey towards accessibility
Design can have a significant impact on delivering accessible experiences to our users. It takes a cultural shift, dedicated experts, and permission to make progress over perfection in order to build momentum. We’ve got a long way to go, but we’re starting to see a real shift in our journey to make GitHub a true home for all developers. ⌘ Read more
Navigation and search improvements for accessibility
Discover the accessibility features within our new navigation and code search which make it easier to use for many more people. ⌘ Read more
Unlocking inclusive design: how Primer’s color system is making GitHub.com more inclusive
How Primer’s updated light and dark theme color contrast strategy resolved hundreds of color-contrast-related accessibility issues over one thousand use cases. ⌘ Read more
Revolutionize your open source workflows: the top 3 reasons why GitHub Codespaces is a must-have for maintainers
GitHub Codespaces is reliable, accessible, and always-ready. Try it out during Maintainer Month and take your projects to new heights! ⌘ Read more
How we work: inclusive retrospectives for the GitHub Accessibility leadership team
Learn about tools and processes the GitHub Accessibility leadership team uses for retrospectives that fully engage every team member. ⌘ Read more
Building a more inclusive GitHub Global Campus
Every student and teacher deserves the same access to GitHub Education offerings. We’ve enlisted GitHub’s Accessibility team to help identify areas for improving inclusivity. ⌘ Read more
They haven’t written the federation code yet. Its literally run on the staging instance. People are paying to access the alpha. Though if you want a code to see what all the fuss is about there are a few with invites around here.
They haven’t written the federation code yet. Its literally run on the staging instance. People are paying to access the alpha. Though if you want a code to see what all the fuss is about there are a few with invites around here.
**RT by @mind_booster: 1/3 🚨Recent @POLITICOEurope leak revealed that US & EU officials have agreed to cooperate on measures to turn public opinion against #encryption.
Experts’ statements by @edri & @globalencrypt have called out against this plan
➡️https://edri.org/our-work/eu-us-plan-offensive-to-legitimise-police-access-to-data-civil-society-responds-amid-growing-fears-press-release/
➡️https://www.globalencryption.org/2023/04/statement-on-eu-us-cooperation-against-encryption/**
1/3 🚨Recent [@POLITICOEurope](https … ⌘ Read more
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
I’m not super a fan of using json. I feel we could still use text as the medium. Maybe a modified version to fix any weakness.
What if instead of signing each twt individually we generated a merkle tree using the twt hashes? Then a signature of the root hash. This would ensure the full stream of twts are intact with a minimal overhead. With the added bonus of helping clients identify missing twts when syncing/gossiping.
Have two endpoints. One as the webfinger to link profile details and avatar like you posted. And the signature for the merkleroot twt. And the other a pageable stream of twts. Or individual twts/merkle branch to incrementally access twt feeds.
Tailscale · Best VPN Service for Secure Networks - Anyone know anything about Tailscale? Used it? Recommend it? How does it stack up in terms of actual secure networking and VPN access to your infra? Can it be trusted
I notice it uses WirGuard™ and is actually written in Go 😅
Docker and Hugging Face Partner to Democratize AI
We’re excited to announce that Happy Face and Docker are partnering to democratize AI and make it more accessible to software engineers! ⌘ Read more
GitHub celebrates the ingenuity of developers with disabilities in new video series
Learn how developers with disabilities are pushing the boundaries of accessibility with ingenuity, open source, and generative AI on The ReadME Project. ⌘ Read more
How to use your own domain as your BlueSky handle
I recently got access to the BlueSky beta, and decided to poke around to see what it’s all about. I will save the details of what it is and how I feel about it for a different post. However, one of the first things you do when you sign up is choose a username that exists under the bsky.app domain. I have zero interest in another name rush where everyone tries to claim the shortest username possible, so I went with aaronpk.bsky.app rather than trying to get a … ⌘ Read more
GitHub Security Lab audited DataHub: Here’s what they found
The GitHub Security Lab audited DataHub, an open source metadata platform, and discovered several vulnerabilities in the platform’s authentication and authorization modules. These vulnerabilities could have enabled an attacker to bypass authentication and gain access to sensitive data stored on the platform. ⌘ Read more
** Ideas for making accessibility and equity a core part of the software development lifecycle **
In accessibility and the product person I said
we need to make accessibility a core part of our processes
Here, I want to talk about that in more detail. I want to briefly explore what making accessibility a part of core processes looks like, and how that is different from centering access … ⌘ Read more
** Accessibility and the product person **
This post is a slightly modified version of a talk I presented to the product practice at my work. It presents a few ways that product designers and managers can help to move accessibility forward. It is a little bit different than what I normally share, here, but, I thought it may be interesting to some folks.
[![Picture of a slide with the title “Why though?” It also includes a quote from Kat Holmes’ book Mismatch. The quote reads: “There are many challeng … ⌘ Read more