Multi-hued e-reader brings more colour, but less clarity
Book covers, magazines, comics and notes benefit greatly from a colour screen but, for reading, black-and-white technology is still superior. ⌘ Read more
On my blog: Free Culture Book Club — Noir & Blanc, part 2 https://john.colagioia.net/blog/2024/04/20/noir-blanc-2.html #freeculture #bookclub
** books, the end of winter, video games and javascript **
Since my last update I’ve read a handful of books. Some standout reads include Tales from Earthsea, The Other Wind and The Left Hand of Darkness, all by Ursula K. Le Guin. I’d read them all before, accepted for The Other Wind. I thought I’d read The Other Wind, but hadn’t! Chaos: Making a New Science by James Gleick was also a fun read. I liked it for the rabbit holes it invited me down; I’ve been thinking a lot … ⌘ Read more
On my blog: Free Culture Book Club — Noir & Blanc, part 1 https://john.colagioia.net/blog/2024/04/13/noir-blanc-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — In Unexpected Places https://john.colagioia.net/blog/2024/04/06/unexpected.html #freeculture #bookclub
On my blog: Free Culture Book Club — Airlock Bound, part 2 https://john.colagioia.net/blog/2024/03/30/airlock-bound-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — Airlock Bound, part 1 https://john.colagioia.net/blog/2024/03/23/airlock-bound-1.html #freeculture #bookclub
UDF is where its at. Not some silly red or blue book that cant even have more than 8+3 filenames!
UDF is where its at. Not some silly red or blue book that cant even have more than 8+3 filenames!
More basement:
I completely forgot that DVD-RAM was a thing once. Found my old disks and they still work. 🤯 The data on them is from 2008, so they’re not that old. Still impressive.
The disks are two-sided. On the photo, that particular side of the disk on the left appears to be completely unused. 🤔
And then I read on Wikipedia that DVD-RAMs aren’t produced anymore at all today. Huh.
(I refuse to tag this as “retrocomputing”. Read/write DVDs that you can use just like a harddisk, thanks to UDF, are still “new and fancy” in my book. 😂)
On my blog: Free Culture Book Club — Cauac Ox https://john.colagioia.net/blog/2024/03/16/cauac-ox.html #freeculture #bookclub
On my blog: Free Culture Book Club — WNV Universe — Other https://john.colagioia.net/blog/2024/03/09/wnv-universe-4.html #freeculture #bookclub
On my blog: Free Culture Book Club — WNV Universe — Woethief 3 https://john.colagioia.net/blog/2024/03/02/wnv-universe-3.html #freeculture #bookclub
Asked an “AI Assistant” (Perplexity) to summarize my introduction of my homepage and then I asked it to give me some book recommendations I might like, and the thing actually nailed it.
My assistant book us seat on the plane that are meant for the crew
‘I would rather walk to my destination’ ⌘ Read more
‘Unforgivable’: Donald Trump won’t ‘protect’ Prince Harry
Former US president Donald Trump revealed if he is re-elected he will not protect Prince Harry from allegations he lied on his US visa application.
When applying for a visa, applicants must disclose their past drug use, and the Prince famously revealed in his book ‘Spare’ that he took drugs.
However, sources close to Harry claim he answered truthfully on his application, and there is no … ⌘ Read more
A chat with author Morgan Richard Olivier
A best-selling author with an eye for wellness and an ear for motivational speaking recently published a new book called “The Strength That Stays.” For Morgan Olivier, the newest literature has served as therapy for both herself and her audiences. ⌘ Read more
On my blog: Free Culture Book Club — WNV Universe — Woethief 2 https://john.colagioia.net/blog/2024/02/24/wnv-universe-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — WNV Universe — Woethief 1 https://john.colagioia.net/blog/2024/02/17/wnv-universe-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — Moria’s Race https://john.colagioia.net/blog/2024/02/10/morias-race.html #freeculture #bookclub
** Two good stories **
I just finished reading The Adventures of Amina al-Sirafi. I loved it. When I finished A Memory Called Empire I assumed it’d be my most favorite book of the year — it has already been unseated!? I mean, if I kept track of favorites. As I finished The Adventures of Amina al-Sirafi I immediately wanted more, so looked to see if there is a sequel (alas, no (or not yet, I hope!?)). I’ve got a gigantic l … ⌘ Read more
On my blog: Free Culture Book Club — Pointy Chances https://john.colagioia.net/blog/2024/02/03/pointy-chances.html #freeculture #bookclub
Chess puzzle book generator: https://www.codemadness.org/chess-puzzles.html
On my blog: Free Culture Book Club — Gedichte https://john.colagioia.net/blog/2024/01/27/gedichte.html #freeculture #bookclub
On my blog: Free Culture Book Club — Space Rover, part 2 https://john.colagioia.net/blog/2024/01/20/space-rover-2.html #freeculture #bookclub
Update on my Fibre to the Premise upgrade (FTTP). NBN installer came out last week to install the NTD and Utility box, after some umming and arring, we figured out the best place to install it. However this mean he wasn’t able to look it up to the Fibre in the pit, and required a 2nd team to come up and trench a new trench and conduit and use that to feed Fibre from the pit to the utility box.
I rang up my ISP to find out when this 2nd team was booked, only to discover to my horror and the horror of my ISP that this was booked a month out on the 2rd Feb 2024! 😱
After a nice small note from my provider to NBN, suddenly I get a phone call and message from an NBN team that do trenching to say it would be done on Saturday (today). That got completed today (despite the heavy rain).
Now all that’s left is a final NBN tech to come and hook the two fibre pieces together and “light it up”! 🥳
On my blog: Free Culture Book Club — Space Rover, part 1 https://john.colagioia.net/blog/2024/01/13/space-rover-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — Ada & Zangemann https://john.colagioia.net/blog/2024/01/06/ada-zangemann.html #freeculture #bookclub
On my blog: Free Culture Book Club — Admin https://john.colagioia.net/blog/2023/12/30/admin.html #freeculture #bookclub
@xuu@txt.sour.is Despite that these AoC math text problems are rather silly in my opinion (reminds me of an exercise in our math book where somebody wanted to carry a railroad rail around an L-shaped corner in the house and the question was how long that rail could be so that it still fits — sure, we’ve all carried several meter long railroad rails in our houses by ourselves numerous times…), these algorithms are really neat!
On my blog: Free Culture Book Club — Only One https://john.colagioia.net/blog/2023/12/23/only-one.html #freeculture #bookclub
Download Over 900 eBooks of Classics Free from StandardEbooks
If you’re interested in doing some reading of the classics, you may appreciate the Standard Ebooks project, which offers free high quality ebooks that are well-formatted, proofread, and professionally designed using style manuals. Standard Ebooks focuses on books that are in the public domain and without copyright restrictions, which is how they’re able to offer … [Read More](https://osxdaily.com/2023/12/21/dow … ⌘ Read more
Download Over 900 eBooks of Classics Free from StandardEbooks
If you’re interested in doing some reading of the classics, you may appreciate the Standard Ebooks project, which offers free high quality ebooks that are well-formatted, proofread, and professionally designed using style manuals. Standard Ebooks focuses on books that are in the public domain and without copyright restrictions, which is how they’re able to offer … [Read More](https://osxdaily.com/2023/12/21/dow … ⌘ Read more
On my blog: Free Culture Book Club — A Vessel for Offering, part 4 https://john.colagioia.net/blog/2023/12/16/vessel-offering-4.html #freeculture #bookclub
On my blog: Free Culture Book Club — A Vessel for Offering, part 3 https://john.colagioia.net/blog/2023/12/09/vessel-offering-3.html #freeculture #bookclub
On my blog: Free Culture Book Club — A Vessel for Offering, part 2 https://john.colagioia.net/blog/2023/12/02/vessel-offering-2.html #freeculture #bookclub
The best gift anyone could give me is the time to be able to finish reading some books.
On my blog: Free Culture Book Club — A Vessel for Offering, part 1 https://john.colagioia.net/blog/2023/11/25/vessel-offering-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — Homestuck, part 3 https://john.colagioia.net/blog/2023/11/18/homestuck-3.html #freeculture #bookclub
On my blog: Free Culture Book Club — Homestuck, part 2 https://john.colagioia.net/blog/2023/11/11/homestuck-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — Homestuck, part 1 https://john.colagioia.net/blog/2023/11/04/homestuck-1.html #freeculture #bookclub
On the book wishlist: https://solar.lowtechmagazine.com/2023/10/thematic-book-series-how-to-downsize-a-transport-network/
On my blog: Free Culture Book Club — Duelyst https://john.colagioia.net/blog/2023/10/28/duelyst.html #freeculture #bookclub
On my blog: Free Culture Book Club — Sugar the Robot, part 2 https://john.colagioia.net/blog/2023/10/21/roboteers-2.html #freeculture #bookclub
http://cdg.neocities.org Come visit my website with a guest book and alternative news from around the world! â»
On my blog: Free Culture Book Club — Sugar the Robot, part 1 https://john.colagioia.net/blog/2023/10/14/roboteers-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — ½ https://john.colagioia.net/blog/2023/10/07/half.html #freeculture #bookclub
On my blog: Free Culture Book Club — Full Bloom https://john.colagioia.net/blog/2023/09/30/full-bloom.html #freeculture #bookclub
Book Podcasts
 ⌘ Read more
⌘ Read more
On my blog: Free Culture Book Club — C-Man https://john.colagioia.net/blog/2023/09/23/c-man.html #freeculture #bookclub
On my blog: Free Culture Book Club — Poles, part 5 https://john.colagioia.net/blog/2023/09/16/poles-5.html #freeculture #bookclub
On my blog: Free Culture Book Club — Poles, part 4 https://john.colagioia.net/blog/2023/09/09/poles-4.html #freeculture #bookclub
On my blog: Free Culture Book Club — Poles, part 3 https://john.colagioia.net/blog/2023/09/02/poles-3.html #freeculture #bookclub
On my blog: Free Culture Book Club — Poles, part 2 https://john.colagioia.net/blog/2023/08/26/poles-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — Poles, part 1 https://john.colagioia.net/blog/2023/08/19/poles-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — Project Ballad, part 3 https://john.colagioia.net/blog/2023/08/12/project-ballad-3.html #freeculture #bookclub
On my blog: Free Culture Book Club — Project Ballad, part 2 https://john.colagioia.net/blog/2023/08/05/project-ballad-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — Project Ballad, part 1 https://john.colagioia.net/blog/2023/07/29/project-ballad-1.html #freeculture #bookclub
On my blog: Free Culture Book Club — Archive of Our Own, part 2 https://john.colagioia.net/blog/2023/07/22/ao3-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — Archive of Our Own, part 1 https://john.colagioia.net/blog/2023/07/15/ao3-1.html #freeculture #bookclub
Important: Lunduke’s Substack shutting down soon! Get to Lunduke’s Locals!
This is absolutely critical: Very soon Lunduke.Substack.com will be shutting down! Replaced entirely by Lunduke.Locals.com! That is already where all of the nerdy articles, podcasts, videos, books, & comics are being published. Locals is where the nerdy party is at! ⌘ Read more
Lunduke Journal Community: Over 21,000 Comments in 2023 (so far)!
While the totally, righteously nerdy articles, podcasts, videos, books, & comics from The Lunduke Journal are awesome… possibly my favorite part of The Lunduke Journal… is the community. On Lunduke.Locals.com we have created one of the most joyous and nerdy communities on planet Earth. A huge thank you to all of you lovely, radical nerds for making it such a fun place to hang out. ⌘ Read more
On my blog: Free Culture Book Club — Someone Like You https://john.colagioia.net/blog/2023/07/08/glider-ink.html #freeculture #bookclub
On my blog: Free Culture Book Club — kiki the nano bot https://john.colagioia.net/blog/2023/07/01/kiki.html #freeculture #bookclub
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
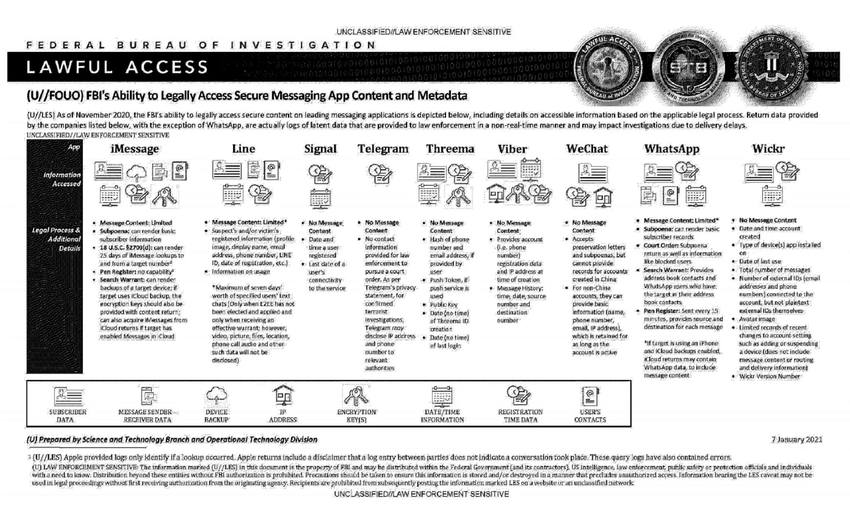
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.

This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
On my blog: Free Culture Book Club — Let’s Move Forward https://john.colagioia.net/blog/2023/06/24/move-forward.html #freeculture #bookclub
On my blog: Free Culture Book Club — Green Comet, part 3 https://john.colagioia.net/blog/2023/06/17/green-comet-3.html #freeculture #bookclub
On my blog: Free Culture Book Club — Green Comet, part 2 https://john.colagioia.net/blog/2023/06/10/green-comet-2.html #freeculture #bookclub
On my blog: Free Culture Book Club — Green Comet, part 1 https://john.colagioia.net/blog/2023/06/03/green-comet-1.html #freeculture #bookclub
** week notes **
Last year I set out to rekindle my reading habit. That went well. This year’s reading has been enjoyable, but I’m not cozy with the ratio of non-fiction to fiction I’ve read this year…non-fiction (especially of the computing persuasion) far out balances the fiction I’ve read. I think this is mostly because I’ve been mired amidst a fiction book that I’ve found to be a slog…but enjoyable, too. I’d have abandoned it and moved on, elsewise. Onward!
Spring is quickly making way to summer h … ⌘ Read more
On my blog: Free Culture Book Club — Distress Beacon https://john.colagioia.net/blog/2023/05/27/distress-beacon.html #freeculture #bookclub
books
On my blog: Free Culture Book Club — Death off the Cuff https://john.colagioia.net/blog/2023/05/20/death-cuff.html #freeculture #bookclub
On my blog: Free Culture Book Club — Jectoons Random Vignettes https://john.colagioia.net/blog/2023/05/13/vignettes.html #freeculture #bookclub
On my blog: Free Culture Book Club — Expedition Sasquatch, part 3 https://john.colagioia.net/blog/2023/05/06/sasquatch-3.html #freeculture #bookclub
Here I am, looking at my bookshelf, where the ‘12 rules for life’ book sits.
I found the way he had to be put in a coma to get off addiction to his medicine etc fascinating. It felt like the good old ‘do as I say, not as I do’ type of thing. But hey - regardless of who you are or how strong you portray yourself - there can always be hard issues to tackle in life.
On my blog: Free Culture Book Club — Expedition Sasquatch, part 2 https://john.colagioia.net/blog/2023/04/29/sasquatch-2.html #freeculture #bookclub
RT by @mind_booster: “Beers and burger’s book club”
Lamego
Quarto encontro
“Beers and burger’s book club”
Lamego
Quarto encontro
⌘ Read moreOn my blog: Free Culture Book Club — Expedition Sasquatch, part 1 https://john.colagioia.net/blog/2023/04/22/sasquatch-1.html #freeculture #bookclub
wait WHY is “book” “libro” in esperanto, but “library” is not “libraro” but “biblioteko”? Huh???
RT by @mind_booster: The Mousetrap 70th Anniversary Edition #Books #AgathaChristie https://paulasimoesblog.wordpress.com/2023/04/18/the-mousetrap-70th-anniversary-edition-books-agathachristie/
The Mousetrap 70th Anniversary Edition #Books #AgathaChristie paulasimoesblog.wordpress.co…
. This has now been fixed, so you can place your orders now!
The issue was that there was a silent API update that kept addresses from validating states and provinces. Note that if your order placed, it’s all okay, this is only for people for whom the site would not let place an order.
… ⌘ Read more
There is a Polish saying that great Polish literature requires three people to suffer: the main character, the writer and the reader. If all three are suffering book becomes part of the school curriculum. A genius at suffering | Hacker News
On my blog: Free Culture Book Club — Life Blood, chapters 23 – 25 https://john.colagioia.net/blog/2023/02/18/life-blood-8.html #freeculture #bookclub
** Accessibility and the product person **
This post is a slightly modified version of a talk I presented to the product practice at my work. It presents a few ways that product designers and managers can help to move accessibility forward. It is a little bit different than what I normally share, here, but, I thought it may be interesting to some folks.
[ ⌘ Read more
⌘ Read more
On my blog: Free Culture Book Club — Life Blood, chapters 20 – 22 https://john.colagioia.net/blog/2023/02/11/life-blood-7.html #freeculture #bookclub
**RT by @mind_booster: Anniversary: Charles Dickens Books to Download #PublicDomain♥
https://paulasimoesblog.wordpress.com/2014/02/07/anniversary-charles-dickens-books-to-download-publicdomain-%e2%99%a5/**
Anniversary: Charles Dickens Books to Download #PublicDomain ♥
![](https://nitter.net/pic/card_img%2F16229117 … ⌘ Read more