I have a very old inspired with two-ish nodes. Though you have to be on the DN42 network to reach it.
@prologic@twtxt.net yes.. But have I? And all the other pods and registries?
Is this missing the <>brackets?
That is broken
@prologic@twtxt.net twtxt DM is not a serious DM protocol.
DOUBLE SUBJECT’D’D!!!
Plz i need to know if it was still April fools day someplace when the Tariffs were announced.
i can see your twts here: https://watcher.sour.is/?uri=https://eapl.me/tw.txt
@david@collantes.us.. i see this one but it says its dead. https://watcher.sour.is/?uri=https://ferengi.one/twtxt.txt
it adds users by finding them in feeds mentioning or following. Your URL is already added.
Hmm i am not sure how you got the URL with users at the end..
Hi, So i made a little MVP registry crawler tool for twtxt. It now has a basic UI to play with. It has a somewhat full history back to about 2018-ish. Plus some interesting bits that were timestamped to earlier.
Find it here: https://watcher.sour.is
Code base is found here: https://git.sour.is/sour-is/xt
probably this one https://yarn.girlonthemoon.xyz/user/kat/twtxt.txt
yeah its from Yarn.. should be $VERSION@$COMMIT and its supposed to be replaced with the actual version and commit.
@lyse@lyse.isobeef.org this is 1990’s certified approved
SqliteCache again with a slight tweak. I might have to rethink the hard-coded LIMIT 50.
@bender@twtxt.net nope.. its causing OOM issues currently.
Registry format is its own thing. It takes the regular feed and appends nick \t uri \t to it. Its something that existed before yarn got big. There is still a bit of work but I will put together a ui for it to make it easier to view and navigate.
@eapl.me@eapl.me I am currently working on Implementing a registry that is also a crawler. It finds any feeds that are mentioned or in the follows header.
https://watcher.sour.is/api/plain/twt
https://watcher.sour.is/api/plain/users
I think @prologic@twtxt.net is also working on one.
hmm i need to start storing feed preambles so i can capture metadata like that
Interesting.. so running into an issue where queries only return a partal set of rows if i run in a docker image built from scratch. i have to add the debian root image for it to work. I wonder what file is missing that the root has?
Hmm I think I can come up with some kind of heuristic.. Maybe if the feed is requested and hasn’t updated in the last few mins it adds to the queue. So the next time it will be fresh.
Hmm so looking at the swagger of the registry spec client it seems to just take a “page”.. That seems worse than doing an offset. Lol.
https://github.com/DracoBlue/twtxt-registry/blob/master/src/swagger.json
I’m not much a fan of registry limit/offset paging. I think I prefer the cursor/count method. And starting at zero for first and max for latest.
So smooth. love it!
@doesnm@doesnm.p.psf.lt haha its not coming back. he talked of a stand alone thing like feeds. but not in yarnd
hmm @prologic@twtxt.net how did replying to lyse double up here?
if it hasn’t updated in a while so i put the request rate to once a week it will take some time before i see an update if it happens today.
I need to figure out a way to back off requests to feeds that don’t update often.
tt reimplementation that I already followed with the old Python tt. Previously, I just had a few feeds for testing purposes in my new config. While transfering, I "dropped" heaps of feeds that appeared to be inactive.
I need to import my yarn cache. It’s sitting at about 1.5G in registry format. That should make things interesting…
tt reimplementation that I already followed with the old Python tt. Previously, I just had a few feeds for testing purposes in my new config. While transfering, I "dropped" heaps of feeds that appeared to be inactive.
neat! my watcher is currently sitting at about 75 MB following over 1500 feeds. only about 200 are currently somewhat active.
-rw-r--r--. 1 xuu xuu 69M Mar 25 20:46 twt.db
-rw-r--r--. 1 xuu xuu 32K Mar 25 21:34 twt.db-shm
-rw-r--r--. 1 xuu xuu 5.6M Mar 25 21:34 twt.db-wal
sqlite> select state, count(*) n from feeds group by 1;
hot|7
warm|8
cold|183
frozen|743
permanantly-dead|857
you just haven’t read this yet.
Chapter 14:
Epilogue:
Chapter 12:
Chapter 13:
I haven’t had one since the before times of COVID. I am not sure if my company will have them again for the near future.
Chapter 11 with guest speaker Cori:
Chapter 11 with Alan:
Chapter 10:
Chapter 9:
Chapter 7:
Chapter 8:
@prologic@twtxt.net @andros@twtxt.andros.dev
more examples:
2020 Jan1 New Year's Day @yearly
2020 jan 3Mon Dr. Martin Luther King, Jr Day @yearly
2020 feb 3Mon President's Day @yearly
2020 may -1Mon Memorial Day @yearly
2020 jun19 Juneteenth @yearly
2020 jul1 Independence Day @yearly
2020 jul24 Pioneer Day @yearly
2020 sept 1Mon Labor Day @yearly
2020 oct 2Mon Columbus Day @yearly
2020 nov11 Veteran's Day @yearly
2020 nov 4Thur Thanksgiving Day @yearly
2020 dec25 Christmas Day @yearly
2025-01 Fri [ ] Take out Trash @weekly
2024-10-17 Thu [x] (A) Did this and that completed:2024-10-18
2025-10-18
[ ] (A) Submit important papers
[ ] (B) Work on +ProjectB
- some note
2024-10-21
- some notes about things to remember for Monday
[ ] Do that
[ ] Travel the stars
@prologic@twtxt.net Chapter 6:
Chapter 2:
Chapter 4: Chapter 5:
ah crap. chapters 2, 4 and 5 are being cropped by yarn on upload. they should be more like 2-3 hours long
@prologic@twtxt.net chapter 5:
I have a file with US holidays but I think it’s on my laptop still
Like
2025-01 Fri [ ] Take out Trash @weekly
For a task that starts the first Friday of January and repeats weekly.
Yeah. It’s mostly a parser at the moment. But I have extended the calendar.txt to include todo.txt and a repeat syntax to generate future occurances of events and todos.
Chapter 3:
Chapter 4:
so dry.. haha this would put me to sleep
Chapter 1:
Chapter 2:
if you want a different voice let me know which to use: https://rhasspy.github.io/piper-samples/
@prologic@twtxt.net I created a script for your book. i have only done the first two chapters. have to do some adjustments to the text so it sounds ok and that takes time..
yarnd pods that form a "distributed network".
@prologic@twtxt.net how come when you reply to eapl.me it doubles up? bug?
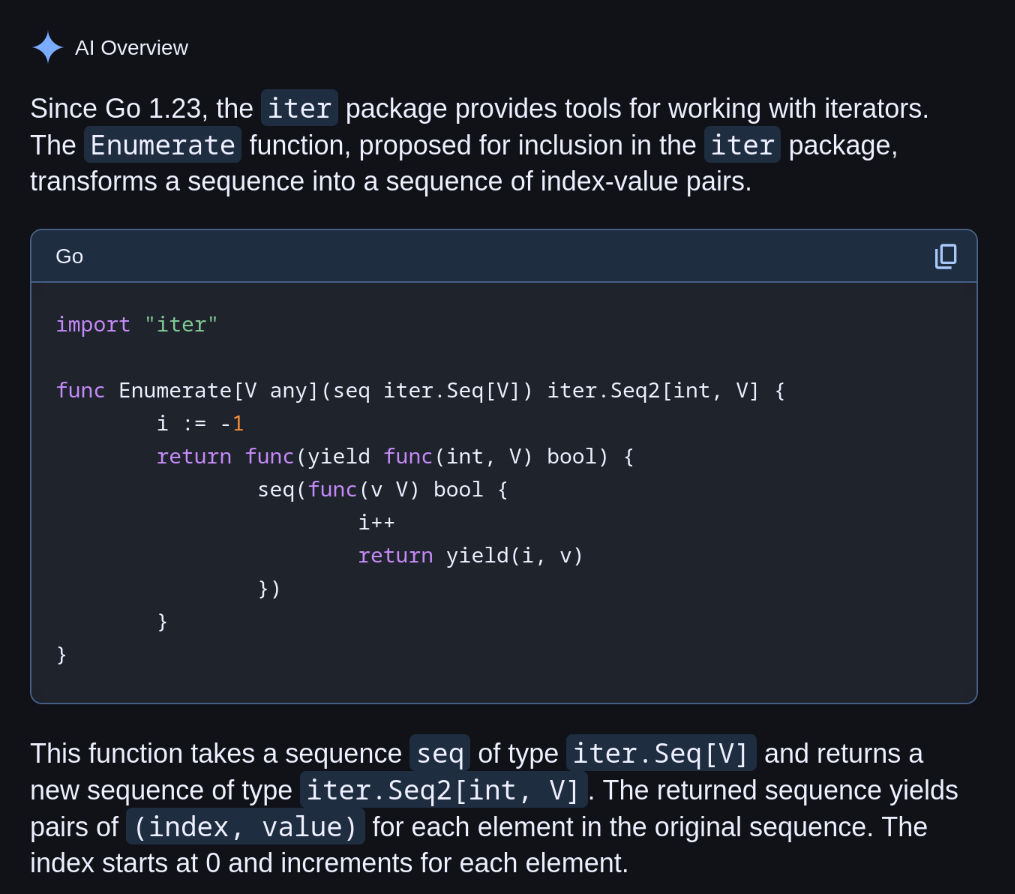
re reading so NewRAMStorage(…) is just something that setups your storage and initial data.. that can probably live with storage/sqlite. The point is the storage package does not import the implementations of storage.Storage It just defines the contract for things that use that interface. Now storage/sqlite CAN import storage and not have a circle dep.
It kinda works in reverse for import directions. usually you have your root package that imports things from deeper in the directory structures.. but for the case of interfaces it reverses where the deeper can import from parents but parents cannot import from children.
- app < storage
< storage/sqlite
< controller < storage
< storage/sqlite
- sqlite < storage
- storage X storage/sqlite
@lyse@lyse.isobeef.org OK. So how I have worked things like this out is to have the interface in the root package from the implementations. The interface doesn’t need to be tested since it’s just a contract. The implementations don’t need to import storage.Storage
- storage/ defines the
Storageinterface (no tests!)
- storage/sqlite for the sqlite implementation tests for sqlite directly
- storage/ram for the ram implementation and tests for RAM directly
- storage/sqlite for the sqlite implementation tests for sqlite directly
- controller/ can now import both storage and the implementation as needed.
So now I am guessing you wanted the RAM test for testing queries against sqlite and have it return some query response?
For that I usually would register a driver for SQL that emulates sqlite. Then it’s just a matter of passing the connection string to open the registered driver on setup.
https://github.com/glebarez/go-sqlite?tab=readme-ov-file#connection-string-examples
maybe even an internal that has the shared test stuff
oof that sucks man. does it make sense to have a separate testutils package to import from?
it seems to be confused with the subject right next to it.. it works better at the end of the twt string.
Yarn won’t display anything. but the parser does add it to the AST in a way that you can parse it out using twt.Attrs().Get("lang")
https://git.mills.io/yarnsocial/go-lextwt/src/branch/main/ast.go#L1270-L1272
https://git.mills.io/yarnsocial/go-types/src/branch/main/twt.go#L473-L478
TwtAttrs
https://git.mills.io/yarnsocial/go-lextwt/pulls/17
Actually it was your old feed on eapl.mx
TwtAttrs
https://git.mills.io/yarnsocial/go-lextwt/pulls/17
Actually it was your old feed on eapl.mx
@eapl.me@eapl.me@eapl.me@eapl.me I saw a few a while back.
For point 1 and others using the metadata tags. we have implemented them in yarnd as [lang=en][meta=data]
Yeah so disappointed. Brother was one of the last good ones.
@prologic@twtxt.net Got you bro.
interesting.. my pod was looking for him as https://eapl.me/twtxt.txt but the correct path is https://eapl.me/tw.txt
I think @movq@www.uninformativ.de removed support for it in jenny. 🫠
@prologic@twtxt.net eapl.me comes up not found for me.
2025-03-02T13:20:00-07:00 (#<fmgas3a https://twtxt.net/user/prologic/twtxt.txt?t=2025-03-02T10:12:13Z>) @<prologic https://twtxt.net/user/prologic/twtxt.txt> its hard to change by consensus. Some things are won in implementation.
True. Though if the idea turns out to be better.. then community will adopt it.
if you look at the subject for that twt you will see that it uses the extended hash format to include a URL address.
A SMART TOILET ON THE ROOF!

I hate to say it .. but we as a species have peaked at this moment. It’s all down hill from here.
@prologic@twtxt.net its hard to change by consensus. Some things are won in implementation.
- System Design Interview Vol. 1 and 2, Alex Xu and Sahn Lam
- Designing Data-Intensive Applications, Martin Kleppmann
I agree. finding good writings on architecture is hard to find. I used to read architecture reviews over on the high scalability blog. i suspect the reason why is that the arch is how the big tech companies can build moats around their bases. I know in AWS world it only goes as far as how to nickle and dime you to death.
I have the books but they don’t grow much more past interview level.
@bender@twtxt.net Y U Relpy @twtxt.net@twtxt.net?
Very borked. should be #xi2cema but seems to be
Why you got to lie to me Google?
oh dang.. i thought i had parsing for !tag from back when someone was using it for his wiki pages.
i guess i left it out. though shouldnt be to hard to add it back in
huh. i suppose. So they came up with mentioning with a bang? i think we parse them as something that i guess we can check for in the AST
I was against them back when all the morons in the press took him at face value that he had nothing to do with it .
@prologic@twtxt.net I’ll have you know it took me minutes of time to get the mouse suspended like that by that rats nest!
@prologic@twtxt.net huh.. i added sour.is and img.sour.is to my whitelist but its not showing inline for me
trying to keep it simple but.. perhaps it can be extended to fix timestamp formats like using " " instead of "T"
i made a little twtxt feed fixer for when a feed uses other whitespace instead of tabs.
@prologic@twtxt.net the code block is the cause of https://txt.sour.is/twt/zn2kg7q
and the second? i get POST errors when i try to submit the webform.
@andros@twtxt.andros.dev lol nice! emacs is wild. text and graphics all inline.
you rehash the same data too much :P
~10 seconds means it had to fire up Qwen 2.8b and prompt it what items would reasonably show up in a right click menu for the desktop.
@prologic@twtxt.net we need to remove: https://git.mills.io/yarnsocial/go-lextwt/src/branch/main/ast.go#L776-L784
apparently i can’t make the edit via gitea.. i am guessing its hitting one of your firewall rules.
alert the twt police!!
@prologic@twtxt.net hmm this isnt right..