@movq@www.uninformativ.de the true 7 bit ascii
I picked up a tiny nuc a bit ago with 64G ram and 16 ryzen cores.
How much CPU you got in the server farm? I thought you had a whole rack.
Woh.. never heard of it. Growing up it was always just the MS EDIT.EXE or for more advanced stuff Nortons editor.
I need to get influxdb up on my router. But I do about .5TB per week. So seems pretty on par to you with all that streaming the family does.
@movq@www.uninformativ.de that is soo much traffic. I don’t think I have ever broken 1TB /mo across my VMS ever.
@prologic@twtxt.net was this in reply to a different thread? Or maybe a hash collision?
@prologic@twtxt.net laughs.. I’m in danger.
@abucci@anthony.buc.ci excellent work on embedding the YO in Hello
@abucci@anthony.buc.ci @prologic@twtxt.net neat.. I saw this one quite a while ago. it is strictly line of sight and blocked by walls or things. The use cases were to have it integrated in the lights in a room and provide super fast connections to devices in an office or coffee shop.
@abucci@anthony.buc.ci my last experience with it was with a Debian package which is known for being out of date :-D
My home ISP has had a few prefixes allocated. They haven’t rolled of out yet because their custom CRM system needs to be updated to be able to allocate/bill for it. Along other reasons they gave when I asked last.
@abucci@anthony.buc.ci does fail2ban work with ipv6 yet?
tmux a would just create a new session if there's no session already to attach to. I probably do that once a day.
@hecanjog@hecanjog.com I have a script for tmux that sets up a new if needed among other things.
http://github.com/brandur/tmux-extra
Works great with powerline.
I suppose to lesson confusion I would rename Is to Because
So you would have:
type ErrPermissionNotAllowed []Permission
func (perms ErrPermissionNotAllowed) Is(permission Permission) bool {
for _, p := range perms {
if p == permission { return true }
}
return false
}
var err error = errPermissionNotAllowed{"is-noob"}
if errors.Is(err, ErrPermissionNotAllowed{}) { ... } // user is not allowed
var e ErrPermissionNotAllowed
if errors.As(err, e) && e.Is("a-noob") { ... } // user is not allowed because they are a noob.
@lyse@lyse.isobeef.org do you need to have an explicit Is function? I believe errors.Is has reflect lite and can do the type infer for you. The Is is only really needed if you have a dynamic type. Or are matching a set of types as a single error maybe? The only required one would be Unwrap if your error contained some other base type so that Is/As can reach them in the stack.
As is perfect for your array type because it asserts the matching type out the wrap stack and populates the type for evaluating its contents.
You can have Error return just “permission not allowed” if the array is empty. It would print the same as the first.
Why not just always use the second one?
@prologic@twtxt.net is goryon not in the google app store?
yeah.. i guess he upped that… but scrolling for a bit can burn through that quite quickly.
If you are going to compare iPhone with android you can’t just throw out bargan bin android phones.. Should compare within the same price points like the Pixel, Galaxy, Pine, or OnePlus models.
Funny.. I would never buy an iPhone again. My wife switched back this last phone update and I can’t stand the interface.
Whelp. The suckification of social media is continuing to expand. Twitter only allows 600 tweets per day unless you pay and then its 6k per day.
An official FBI document dated January 2021, obtained by the American association “Property of People” through the Freedom of Information Act.
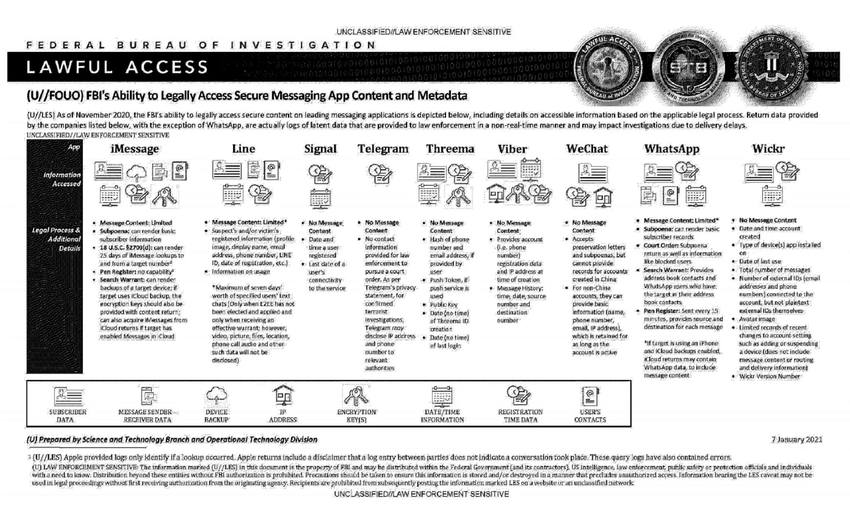
This document summarizes the possibilities for legal access to data from nine instant messaging services: iMessage, Line, Signal, Telegram, Threema, Viber, WeChat, WhatsApp and Wickr. For each software, different judicial methods are explored, such as subpoena, search warrant, active collection of communications metadata (“Pen Register”) or connection data retention law (“18 USC§2703”). Here, in essence, is the information the FBI says it can retrieve:
Apple iMessage: basic subscriber data; in the case of an iPhone user, investigators may be able to get their hands on message content if the user uses iCloud to synchronize iMessage messages or to back up data on their phone.
Line: account data (image, username, e-mail address, phone number, Line ID, creation date, usage data, etc.); if the user has not activated end-to-end encryption, investigators can retrieve the texts of exchanges over a seven-day period, but not other data (audio, video, images, location).
Signal: date and time of account creation and date of last connection.
Telegram: IP address and phone number for investigations into confirmed terrorists, otherwise nothing.
Threema: cryptographic fingerprint of phone number and e-mail address, push service tokens if used, public key, account creation date, last connection date.
Viber: account data and IP address used to create the account; investigators can also access message history (date, time, source, destination).
WeChat: basic data such as name, phone number, e-mail and IP address, but only for non-Chinese users.
WhatsApp: the targeted person’s basic data, address book and contacts who have the targeted person in their address book; it is possible to collect message metadata in real time (“Pen Register”); message content can be retrieved via iCloud backups.
Wickr: Date and time of account creation, types of terminal on which the application is installed, date of last connection, number of messages exchanged, external identifiers associated with the account (e-mail addresses, telephone numbers), avatar image, data linked to adding or deleting.
TL;DR Signal is the messaging system that provides the least information to investigators.
Ol Ben sets himself up as an intellectual for the right. He got promoted up with his connections with PragerU. Talks like he is the smartest one in the room. Though his arguments are full of logical fallacies. He is up there with Joe Rogan and the ilk destroying rational though in America.
@prologic@twtxt.net The hackathon project that I did recently used openai and embedded the response info into the prompt. So basically i would search for the top 3 most relevant search results to feed into the prompt and the AI would summarize to answer their question.
But remember the LLM is only a very good auto complete.
Most of the can run locally have such a small training set they arnt worth it. Are more like the Markov chains from the subreddit simulator days.
There is one called orca that seems promising that will be released as OSS soon. Its running at comparable numbers to OpenAI 3.5.
Boy, the quality of Time is fallen from when it was the Time of its Time to being nearly the Time of our Time!
Man.. Putin is really becoming the ‘Stalin’ of Russia!
Sad to see it come crashing down
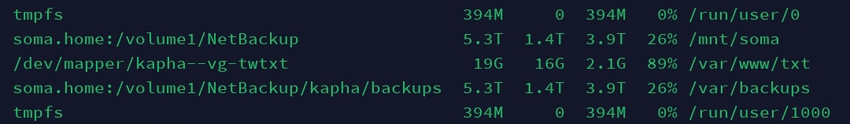
Just local NAS currently
@mckinley@twtxt.net ninja backup and Borg
@prologic@twtxt.net that would work if it was using shamir’s secret sharing .. although i think its typically 3 of 5 so you get 3, one to the company, and one to the “third party”. so you can recover all you want.. but if the company or 3rd wants to they need one of your 3 to recover.
but still .. if they are providing them then whats the point of trusting they don’t have copies.
@movq@www.uninformativ.de § after we pass the key over to the GOV cloud for our protection.
@abucci@anthony.buc.ci buuuuut it show when winter!
In the time scale viewed from the planets perspective, the climate has changed many many times.. The issue is whether that change that will inevitability come is hospitable to us meat bags. Or if we are doomed to take part in the next mass extinction event.
@movq@www.uninformativ.de @prologic@twtxt.net you think we could get media cards to show youtube previews?
I setup Joplin with caddy as the WebDAV server. Works okay. The e2e encryption can get messed up sometimes. Supports markdown and images.
@prologic@twtxt.net hey.
@abucci@anthony.buc.ci read my new skibloreet about why social meets payments is the next level idea! For just §5 bitshlongs a month on my serfdomage site!
Also a interesting contender. https://store.minisforum.com/products/minisforum-um773-lite?variant=43717641994485
ECC ram would make it perfect.
@shreyan@twtxt.net probably ~1k up to 1.5k. One I found had 64G ram and 12C / 16T for 1.1k
@prologic@twtxt.net have trued to get a RasPi lately? Them things are Unobtainium